Cybercriminal Accused Of Millions In Office365 Account Compromises
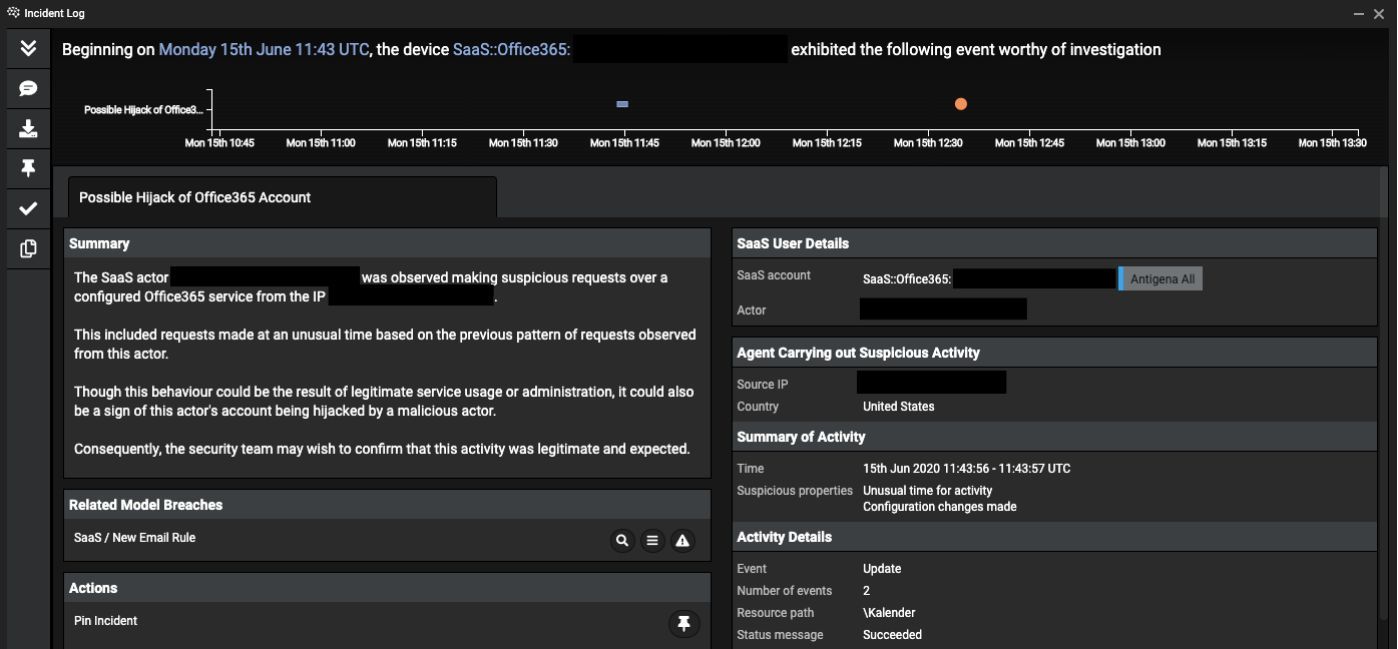
Table of Contents
The Accused Cybercriminal and Their Modus Operandi
The alleged cybercriminal, whose identity remains undisclosed at this time, is accused of employing sophisticated techniques to gain unauthorized access to numerous Office365 accounts. The scale of the operation is unprecedented, impacting businesses and individuals across multiple geographical regions.
Methods of Compromise
The accused allegedly utilized a combination of tactics to breach Office365 security:
- Phishing Attacks: Highly convincing phishing emails were deployed, mimicking legitimate communications from trusted sources. These emails contained malicious links or attachments leading to malware infections or credential harvesting. Examples include emails appearing to be from internal IT departments requesting password resets or from financial institutions requesting account verification.
- Credential Stuffing: The cybercriminal allegedly used stolen credentials obtained from other data breaches to attempt logins on Office365 accounts. This brute-force method targets accounts with weak or reused passwords.
- Exploiting Vulnerabilities: The investigation suggests exploitation of known vulnerabilities in older versions of Office365 software, highlighting the critical need for regular updates. Specific vulnerabilities exploited are still under investigation.
The operation targeted thousands of accounts, spanning diverse industries and geographic locations, demonstrating a broad and indiscriminate approach.
Financial Gains and Targets
The financial gains from this alleged Office365 account compromise are estimated to be in the millions of dollars. The cybercriminal reportedly targeted a range of businesses and individuals, focusing on those perceived as having less robust security measures in place:
- Data Stolen: The stolen data included sensitive customer information, financial records, intellectual property, and confidential business communications.
- Monetization Methods: The stolen data was allegedly monetized through various methods, including selling it on the dark web and using it for ransomware attacks. In some cases, ransomware was deployed directly onto compromised systems, demanding payment for data recovery.
The Impact of the Office365 Account Compromise
The consequences of this alleged Office365 account compromise extend far beyond the immediate financial losses. Victims are facing substantial challenges in terms of reputation, legal compliance, and ongoing operational disruption.
Financial Losses
The financial impact on victims is substantial:
- Lost Revenue: Businesses experienced significant revenue loss due to operational downtime, data recovery efforts, and damage to customer relationships.
- Legal Fees: Victims incurred substantial costs associated with legal counsel, regulatory investigations, and potential lawsuits.
- Recovery Costs: The cost of recovering and restoring compromised data, as well as implementing enhanced security measures, has been substantial.
Reputational Damage
Data breaches severely erode trust and can inflict lasting damage on reputation:
- Loss of Customer Confidence: Customers may lose trust in businesses that experience data breaches, leading to decreased sales and market share.
- Negative Media Coverage: Negative publicity surrounding the breach can severely damage a company's brand image.
- Impact on Stock Prices: For publicly traded companies, a data breach can result in a significant drop in stock prices.
Legal and Regulatory Consequences
Victims and the accused cybercriminal face serious legal and regulatory ramifications:
- GDPR Fines: Businesses operating within the European Union face potential fines under the General Data Protection Regulation (GDPR) for failing to adequately protect customer data.
- Potential Lawsuits: Victims can pursue legal action against the cybercriminal and, in some cases, against the organizations responsible for the security breach.
- Criminal Charges: The accused cybercriminal faces significant criminal charges for data theft, fraud, and other related offenses.
Protecting Your Business from Office365 Account Compromises
Protecting your Office365 environment requires a multi-layered approach incorporating robust security practices and the right tools.
Best Practices for Office365 Security
Implement these essential security measures:
- Multi-Factor Authentication (MFA): Enable MFA to add an extra layer of security to your Office365 accounts.
- Strong Passwords: Enforce the use of strong, unique passwords for all accounts.
- Regular Security Updates: Keep your Office365 software and all related applications up-to-date with the latest security patches.
- Employee Training: Conduct regular training sessions to educate employees about phishing awareness and safe online practices.
- Robust Access Controls: Implement strong access controls to limit user permissions and prevent unauthorized access to sensitive data.
- Utilize Microsoft's Security Features: Leverage Microsoft's built-in security features, such as advanced threat protection and data loss prevention.
The Role of Cybersecurity Solutions
Investing in robust cybersecurity solutions is crucial:
- Intrusion Detection Systems (IDS): IDS can detect and alert you to suspicious activity within your network.
- Security Information and Event Management (SIEM) systems: SIEM systems collect and analyze security logs to identify and respond to threats.
Incident Response Planning
Having a well-defined incident response plan is paramount:
- Establish Procedures: Create clear procedures for identifying, containing, eradicating, and recovering from a security breach.
- Communication Plan: Develop a communication plan for notifying affected parties, regulatory bodies, and the public.
- Regular Testing: Regularly test your incident response plan to ensure its effectiveness.
Conclusion
The alleged Office365 account compromise underscores the critical need for robust cybersecurity measures. The financial and reputational damage caused by such breaches can be devastating. The cybercriminal's alleged methods, involving phishing attacks, credential stuffing, and exploiting vulnerabilities, highlight the importance of proactive security practices, including multi-factor authentication, strong passwords, regular updates, and employee training. By implementing these best practices and utilizing advanced cybersecurity solutions, businesses can significantly reduce their risk of falling victim to similar attacks. Don't become another victim of Office365 account compromises. Learn more about protecting your business today!

Featured Posts
-
 Selling Sunset Star Exposes La Landlord Price Gouging After Fires
Apr 24, 2025
Selling Sunset Star Exposes La Landlord Price Gouging After Fires
Apr 24, 2025 -
 Trumps Budget Cuts Increase Tornado Risk As Season Begins
Apr 24, 2025
Trumps Budget Cuts Increase Tornado Risk As Season Begins
Apr 24, 2025 -
 Ice Denies Columbia Student Mahmoud Khalils Request To Attend Sons Birth
Apr 24, 2025
Ice Denies Columbia Student Mahmoud Khalils Request To Attend Sons Birth
Apr 24, 2025 -
 Navigating The Complexities Of The Chinese Auto Market Case Studies Of Bmw And Porsche
Apr 24, 2025
Navigating The Complexities Of The Chinese Auto Market Case Studies Of Bmw And Porsche
Apr 24, 2025 -
 Warriors Dominant Performance Extends Hornets Losing Streak To Seven
Apr 24, 2025
Warriors Dominant Performance Extends Hornets Losing Streak To Seven
Apr 24, 2025
Latest Posts
-
 Resi Awards 2025 A Celebration Of Excellence
May 12, 2025
Resi Awards 2025 A Celebration Of Excellence
May 12, 2025 -
 Ipswich Towns Winning Strategy The Chaplin Influence
May 12, 2025
Ipswich Towns Winning Strategy The Chaplin Influence
May 12, 2025 -
 Gerard Hernandez Parle De Sa Relation Avec Chantal Ladesou Dans Scenes De Menages
May 12, 2025
Gerard Hernandez Parle De Sa Relation Avec Chantal Ladesou Dans Scenes De Menages
May 12, 2025 -
 Meet The Winners Of The 2025 Resi Awards
May 12, 2025
Meet The Winners Of The 2025 Resi Awards
May 12, 2025 -
 Analyzing Chaplins Contribution To Ipswich Town Wins
May 12, 2025
Analyzing Chaplins Contribution To Ipswich Town Wins
May 12, 2025
