Dystopian Site Innovations: How Block Mirror Bypasses Censorship And Triggers

Table of Contents
Understanding Block Mirror Technology
Block Mirror employs a sophisticated, yet relatively simple-to-understand, mechanism to circumvent censorship. Instead of relying on a single server, it utilizes a distributed network architecture. This means that mirrored websites are spread across numerous servers globally, making it incredibly difficult for censors to shut down access completely. Think of it like a game of whack-a-mole, but on a massive, international scale.
Key features of Block Mirror include:
- Distributed Network Architecture: This robust design makes Block Mirror resilient to takedown attempts. If one server goes offline, others instantly pick up the slack, ensuring continuous access.
- Robust Encryption Methods: Block Mirror prioritizes user privacy and security by employing strong encryption protocols, protecting user data and maintaining anonymity. This helps users avoid surveillance and tracking.
- Website Mirroring Mechanism: The core functionality of Block Mirror revolves around mirroring websites. This means creating exact copies of blocked websites on multiple servers around the world, making them accessible even if the original site is censored.
- Firewall and Censorship Bypass: Block Mirror cleverly navigates various censorship techniques, such as DNS blocking, IP blocking, and deep packet inspection, to provide users with consistent access to blocked content.
Compared to other censorship bypass methods like VPNs and Tor, Block Mirror offers a unique approach. While VPNs mask your IP address and Tor uses a layered network of relays, Block Mirror focuses on mirroring the content itself, making it more resilient against sophisticated censorship techniques. However, it's important to note that using Block Mirror alongside a VPN or Tor can enhance security and anonymity.
Block Mirror's Effectiveness in Bypassing Censorship
Block Mirror has demonstrated a significant success rate in circumventing various forms of internet censorship. Its distributed nature and encryption make it particularly effective against less sophisticated blocking methods.
- Case Studies: Reports suggest successful bypasses of censorship in countries like China and Iran, where internet access is heavily restricted. While specific examples are often kept confidential for security reasons, anecdotal evidence points to its efficacy.
- Successful Mirroring: Block Mirror has been successfully used to mirror news websites, social media platforms, and even educational resources that are blocked in certain regions.
- Limitations: While highly effective, Block Mirror isn't a foolproof solution. Highly sophisticated censorship techniques, like deep packet inspection combined with advanced AI-driven monitoring, can present challenges. Government-level surveillance and monitoring can also compromise the effectiveness of Block Mirror.
Block Mirror's effectiveness against specific censorship techniques varies. While it generally performs well against DNS and IP blocking, more advanced methods like deep packet inspection require more sophisticated circumvention strategies, often involving the combined use of Block Mirror with other privacy tools.
Ethical Considerations and Potential Misuse of Block Mirror
While Block Mirror offers a powerful tool for accessing information in censored environments, it also presents ethical challenges. Its potential for misuse is a serious concern.
- Double-Edged Sword: The ability to access information freely is a fundamental human right, yet Block Mirror can also facilitate access to illegal content, harmful propaganda, and misinformation. This creates a complex ethical dilemma.
- Free Speech vs. Harmful Content: Block Mirror's role in protecting free speech is undeniable. However, it also presents the risk of enabling the spread of hate speech, violent extremism, and other harmful materials. Balancing these competing interests is crucial.
- Legal and Regulatory Challenges: The use of Block Mirror raises significant legal and regulatory challenges for both users and developers. Governments might attempt to restrict or ban its use, creating a legal grey area.
The Future of Block Mirror and Similar Technologies
The future of Block Mirror and similar technologies is inextricably linked to the ongoing arms race between censorship and circumvention. Innovations on both sides are expected.
- Future Iterations: We can anticipate improvements in encryption, network architecture, and bypass techniques within Block Mirror. More robust methods of resisting advanced censorship are likely to be developed.
- Emerging Technologies: Technologies like decentralized networks, blockchain, and quantum computing could potentially further enhance the ability of tools like Block Mirror to bypass censorship.
- Long-Term Impact: The long-term impact of Block Mirror and similar technologies on internet freedom is significant. They are shaping the future of information access and challenging the power of oppressive regimes.
Conclusion: Dystopian Site Innovations: The Implications of Block Mirror and the Fight for Open Access
Block Mirror presents a powerful, yet complex, tool in the ongoing struggle against internet censorship. Its effectiveness in bypassing restrictions is significant, but its potential for misuse requires careful consideration. The ethical implications of circumventing censorship necessitate a balanced approach, weighing the importance of free information access against the risks of spreading harmful content.
Understanding Block Mirror and its implications is crucial for navigating the complexities of internet censorship. Learn more about this and other tools to protect your right to access information, but always do so responsibly and ethically. The fight for open access continues, and tools like Block Mirror are playing a vital role in this ongoing battle.

Featured Posts
-
 Donde Ver El Partido Roma Monza En Directo
May 16, 2025
Donde Ver El Partido Roma Monza En Directo
May 16, 2025 -
 Maple Leafs 2 1 Win Over Avalanche A Hard Fought Contest
May 16, 2025
Maple Leafs 2 1 Win Over Avalanche A Hard Fought Contest
May 16, 2025 -
 Bvg Mitarbeiter Drohen Mit Streik Die Situation Nach Gescheiterten Verhandlungen
May 16, 2025
Bvg Mitarbeiter Drohen Mit Streik Die Situation Nach Gescheiterten Verhandlungen
May 16, 2025 -
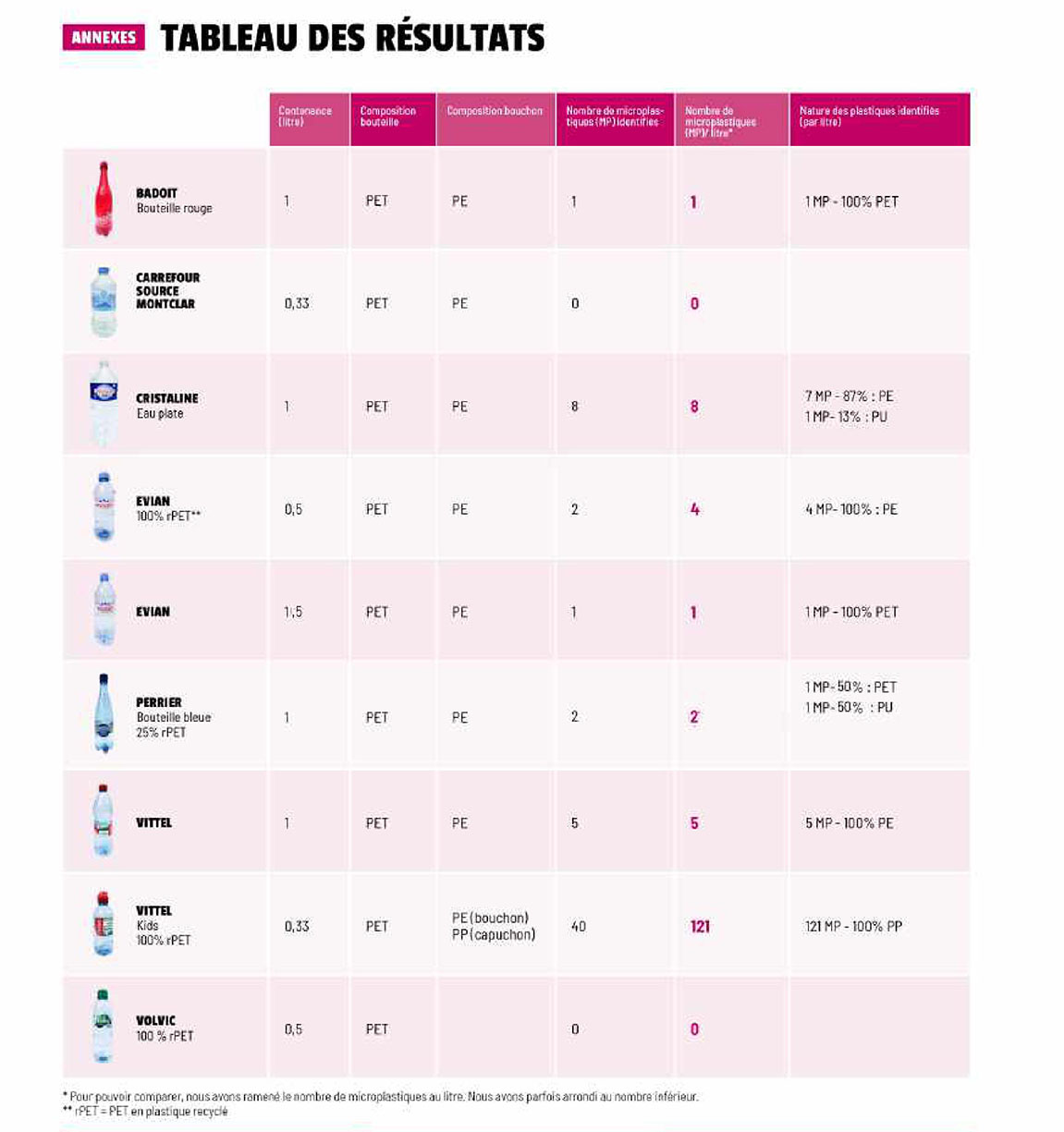 Dove Si Trovano Le Maggiori Concentrazioni Di Microplastiche In Acqua
May 16, 2025
Dove Si Trovano Le Maggiori Concentrazioni Di Microplastiche In Acqua
May 16, 2025 -
 Kid Cudi Auction High Prices For Jewelry And Sneakers
May 16, 2025
Kid Cudi Auction High Prices For Jewelry And Sneakers
May 16, 2025
Latest Posts
-
 Market Chaos The Ultra Wealthy Find Stability In Luxury Real Estate
May 17, 2025
Market Chaos The Ultra Wealthy Find Stability In Luxury Real Estate
May 17, 2025 -
 Trumps Foreign Policy And His Interactions With Arab Leaders
May 17, 2025
Trumps Foreign Policy And His Interactions With Arab Leaders
May 17, 2025 -
 Luxury Real Estates Resilience A Sanctuary For High Net Worth Individuals During Market Downturns
May 17, 2025
Luxury Real Estates Resilience A Sanctuary For High Net Worth Individuals During Market Downturns
May 17, 2025 -
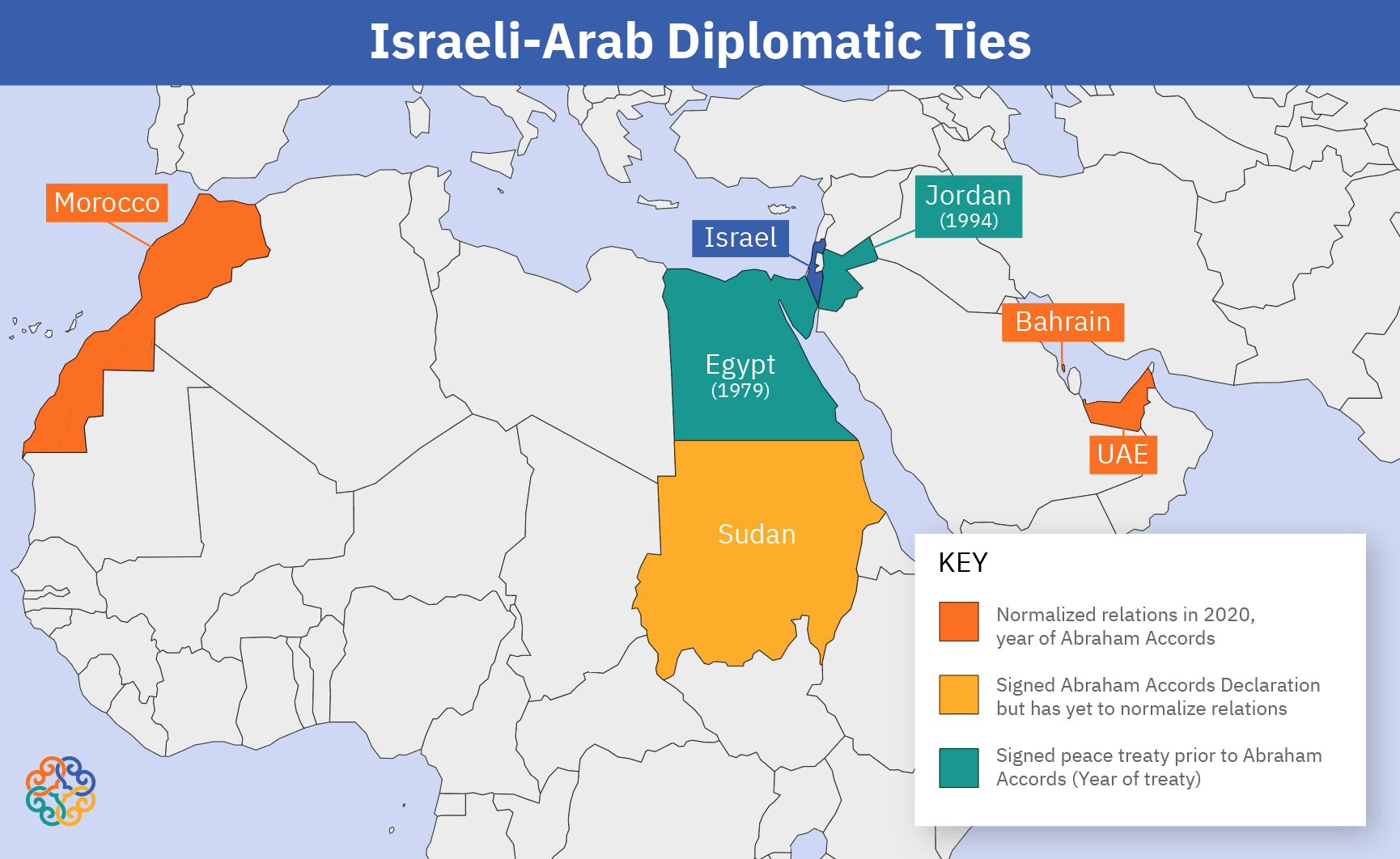 The Nature Of Trumps Relationships With Arab Leaders Handsome Attractive Tough
May 17, 2025
The Nature Of Trumps Relationships With Arab Leaders Handsome Attractive Tough
May 17, 2025 -
 Air Traffic Controllers Exclusive Account Of Near Midair Collision
May 17, 2025
Air Traffic Controllers Exclusive Account Of Near Midair Collision
May 17, 2025
