Exec Office365 Breaches Net Millions For Crook, FBI Claims
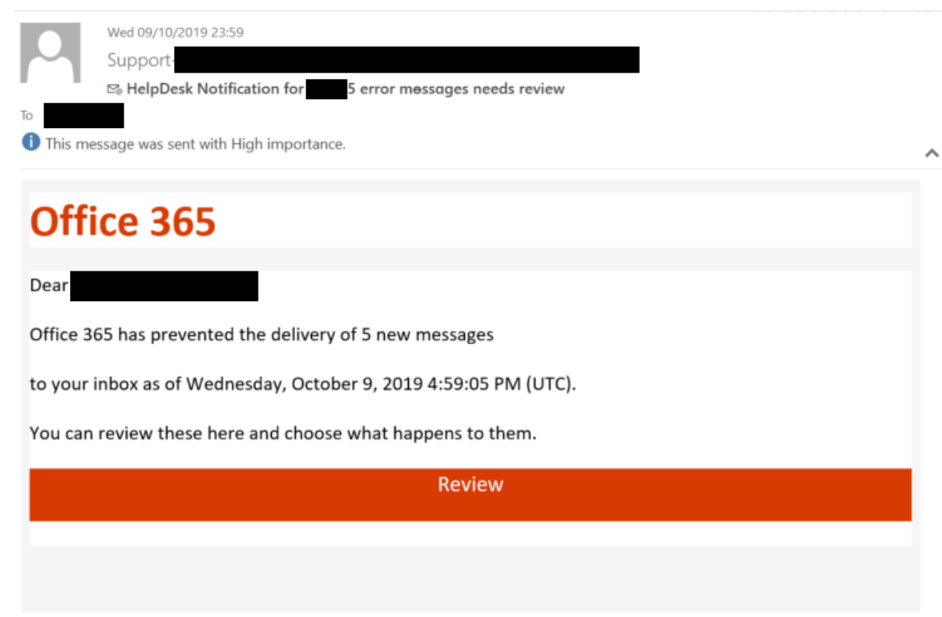
Table of Contents
The Scale of the Problem: Millions Lost Through Office365 Compromise
The FBI's investigation reveals a shocking trend: Office365 has become a prime target for cybercriminals, resulting in millions of dollars in losses for businesses of all sizes. While precise figures are often withheld for security reasons, reports indicate losses in the millions per incident, with a significant upward trend year over year. The number of affected businesses is also substantial, highlighting the widespread vulnerability. This isn't just affecting large corporations; small and medium-sized enterprises (SMEs) are equally at risk.
The growth of Office365 breaches is alarming. Statistics show a dramatic increase in attacks over the past few years, fueled by the platform's widespread adoption and the sophistication of cybercriminal tactics.
- Attack Methods: The methods employed are varied and increasingly sophisticated. Common tactics include:
- Phishing: Deceiving employees into revealing login credentials via seemingly legitimate emails.
- Malware: Installing malicious software to steal data or encrypt systems (ransomware).
- Brute-force attacks: Systematically trying numerous password combinations.
- Data Compromised: The data stolen can include:
- Financial records: Bank details, transaction history, sensitive financial information.
- Intellectual property: Confidential designs, research data, trade secrets.
- Customer data: Personally identifiable information (PII), leading to potential legal ramifications.
- Targeted Industries: While no industry is immune, sectors like finance, healthcare, and technology are frequently targeted due to the high value of their data.
Understanding the Tactics: How Hackers Exploit Office365 Vulnerabilities
Hackers exploit various vulnerabilities to gain access to Office365 accounts. These attacks often leverage a combination of techniques:
-
Social Engineering: This involves manipulating individuals into divulging sensitive information.
- Phishing: Deceptive emails mimicking legitimate communications, often containing malicious links or attachments.
- Pretexting: Creating a false sense of urgency or authority to trick users into cooperating.
-
Malware & Ransomware: Malicious software is used to steal credentials, encrypt data (ransomware), or install backdoors for persistent access.
-
Weak Passwords & MFA Bypasses: Many breaches stem from weak or easily guessed passwords, and a lack of multi-factor authentication (MFA). Hackers utilize various techniques to bypass MFA, including exploiting vulnerabilities in the authentication process.
-
Typical Attack Scenario: A typical attack might involve a phishing email leading to a compromised credential, granting access to an Office365 account. From there, hackers might deploy malware, steal data, or even take control of the entire system. The use of legitimate tools for malicious purposes, such as compromised cloud storage services, is also prevalent.
Protecting Your Business: Strengthening Office365 Security
Proactive security measures are crucial to prevent costly Office365 breaches. Here's how to bolster your defenses:
-
Multi-Factor Authentication (MFA): Implement MFA across all Office365 accounts. This adds an extra layer of security, making it significantly harder for attackers to gain access even with stolen credentials.
-
Strong Password Policies: Enforce strong, unique passwords and encourage the use of password managers. Regular password changes are also essential.
-
Security Awareness Training: Educate your employees about phishing scams, malware threats, and other common attack vectors. Regular training keeps employees vigilant and reduces the risk of human error.
-
Software Updates & Patches: Ensure that all Office365 applications and related software are regularly updated with the latest security patches. This closes known vulnerabilities and reduces the attack surface.
-
Practical Steps:
- Implement strong password policies: Require passwords of at least 12 characters, including uppercase and lowercase letters, numbers, and symbols.
- Use reputable security software: Invest in robust antivirus and anti-malware solutions.
- Utilize Microsoft's security features: Leverage built-in Office365 security tools, such as advanced threat protection.
- Regularly review user permissions: Ensure that only authorized users have access to sensitive data.
The Aftermath: Responding to an Office365 Breach and Recovery
Despite preventative measures, breaches can still occur. Having a robust incident response plan is vital:
-
Incident Response Planning: Develop a comprehensive plan outlining steps to take in the event of a breach.
-
Data Recovery & Business Continuity: Prioritize data backups and have a plan for restoring systems and operations in case of a disruption.
-
Cybersecurity Professionals: Engage the services of experienced cybersecurity professionals to assist with investigation, remediation, and recovery.
-
Immediate Actions:
- Isolate affected systems: Prevent further damage by immediately disconnecting compromised devices from the network.
- Gather evidence: Document all aspects of the breach for investigation and legal purposes.
- Notify relevant authorities: Report the incident to law enforcement and regulatory bodies as required.
- Communicate with affected parties: Inform clients or customers if their data has been compromised.
Conclusion: Preventing Costly Office365 Breaches: Proactive Security is Essential
Office365 breaches are a significant threat, causing substantial financial and reputational damage. The scale of the problem demands proactive security measures. By understanding the common attack methods, implementing strong security controls, and having a robust incident response plan, businesses can significantly reduce their risk. Don't become the next victim of an Office365 data breach. Protect your business from costly Office365 breaches by strengthening your Office365 security today. Invest in robust security measures, train your employees, and stay informed about the latest threats. For further resources and assistance, explore the Microsoft Security Center and consult with reputable cybersecurity firms.

Featured Posts
-
 Shota Imanagas Dominant Splitter Analyzing The Cubs Lefty Weapon
Apr 23, 2025
Shota Imanagas Dominant Splitter Analyzing The Cubs Lefty Weapon
Apr 23, 2025 -
 T Mobiles 16 Million Data Breach Fine Three Years Of Security Failures
Apr 23, 2025
T Mobiles 16 Million Data Breach Fine Three Years Of Security Failures
Apr 23, 2025 -
 Rethinking Middle Management Their Impact On Organizational Performance
Apr 23, 2025
Rethinking Middle Management Their Impact On Organizational Performance
Apr 23, 2025 -
 Dortmunds Adeyemi Ein Dfb Star Mit Stil
Apr 23, 2025
Dortmunds Adeyemi Ein Dfb Star Mit Stil
Apr 23, 2025 -
 127 Years Of Brewing History Ends Anchor Brewing Companys Closure
Apr 23, 2025
127 Years Of Brewing History Ends Anchor Brewing Companys Closure
Apr 23, 2025
