Federal Investigation: Millions Stolen Through Office365 Infiltration

Table of Contents
The Scale of the Office365 Breach and Financial Losses
The Office365 breach under federal investigation resulted in the theft of an estimated $5 million, impacting numerous victims. While specific details about the number of victims remain confidential during the ongoing investigation, sources suggest that several small to medium-sized businesses across multiple states were targeted. The perpetrators specifically focused on businesses handling significant financial transactions, indicating a sophisticated level of targeting.
- Specific examples of financial losses: Victims reported losses ranging from tens of thousands to hundreds of thousands of dollars, with many facing significant operational disruptions.
- Statistics on increasing frequency: Reports indicate a sharp increase in Office365 breaches over the past year, highlighting the growing sophistication and prevalence of these attacks. Experts predict even greater losses in the coming years without improved security practices.
- Long-term effects: The financial impact extends beyond immediate losses; victims face reputational damage, legal ramifications, and the substantial cost of recovery and remediation.
Methods Used in the Office365 Infiltration
The perpetrators employed a multi-pronged approach to gain access to Office365 accounts, combining sophisticated phishing techniques with malware deployment. This wasn't a simple brute-force attack; it demonstrated a high degree of planning and technical expertise.
- Phishing campaigns and social engineering: Highly realistic phishing emails were sent to employees, mimicking legitimate communications from trusted sources. These emails contained malicious links or attachments that, when clicked, installed malware on the victims' systems. Social engineering tactics were used to manipulate employees into divulging sensitive login credentials.
- Malware deployment: Once malware was installed, it acted as a backdoor, granting the perpetrators continuous access to Office365 accounts and corporate networks. This malware likely included keyloggers and data exfiltration tools.
- Exploited vulnerabilities: While specifics are still under investigation, it is likely that the attackers exploited known vulnerabilities in either Office365 itself or in third-party applications integrated with the platform.
The Federal Investigation: Ongoing Efforts and Potential Outcomes
Multiple federal agencies are collaborating on this investigation, including the FBI and the Department of Homeland Security. While the investigation is ongoing, and no arrests have been publicly announced, indictments are anticipated.
- Agencies involved: The multi-agency approach highlights the seriousness of the crime and the commitment to bringing the perpetrators to justice.
- Current status: The investigation is focused on tracing the stolen funds and identifying those responsible for the Office365 infiltration.
- Potential penalties: If convicted, the perpetrators face significant prison sentences and substantial fines under various federal laws related to computer fraud and financial crimes.
Improving Office365 Security: Best Practices for Prevention
Protecting your organization from similar Office365 infiltration attempts requires a multi-layered approach to security.
- Multi-factor authentication (MFA): Enabling MFA is paramount. It adds an extra layer of security, making it significantly harder for attackers to gain access even if they obtain passwords.
- Strong password practices: Enforce the use of strong, unique passwords, and encourage regular password changes. Password managers can help simplify this process.
- Security awareness training: Regular security awareness training for employees is crucial to educating them about phishing scams and other social engineering techniques.
Conclusion
This federal investigation into the millions stolen through Office365 infiltration underscores the critical need for enhanced cybersecurity measures. The attackers employed sophisticated techniques, highlighting the ever-evolving nature of cyber threats. The key takeaways are the importance of implementing multi-factor authentication, promoting strong password hygiene, and investing in comprehensive security awareness training. Don't wait for a similar Office365 infiltration to impact your business. Protect your business from Office365 infiltration today! Learn more about enhancing your Office365 security now and take proactive steps to safeguard your valuable data and financial assets.

Featured Posts
-
 Bmw Porsche And The Complexities Of The Chinese Automotive Landscape
Apr 24, 2025
Bmw Porsche And The Complexities Of The Chinese Automotive Landscape
Apr 24, 2025 -
 Mahmoud Khalil Columbia Student Blocked By Ice From Attending Sons Birth
Apr 24, 2025
Mahmoud Khalil Columbia Student Blocked By Ice From Attending Sons Birth
Apr 24, 2025 -
 Tesla Space X And The Epa How Elon Musk And Doge Changed The Game
Apr 24, 2025
Tesla Space X And The Epa How Elon Musk And Doge Changed The Game
Apr 24, 2025 -
 Nba
Apr 24, 2025
Nba
Apr 24, 2025 -
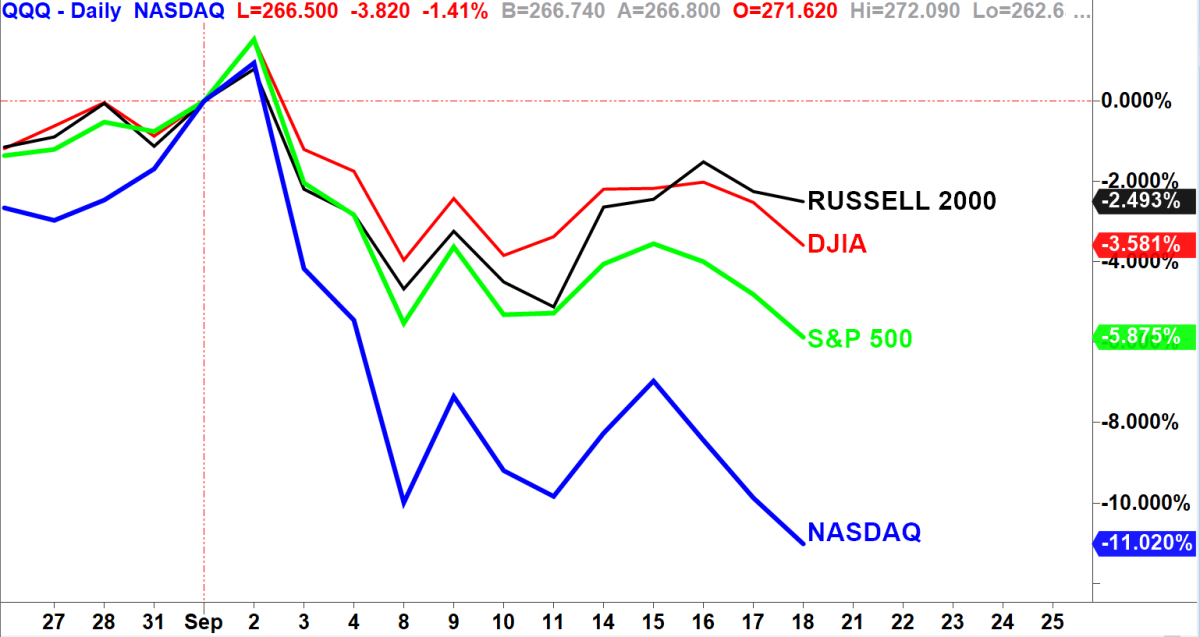 Live Stock Market Data Dow S And P 500 And Nasdaq For April 23rd
Apr 24, 2025
Live Stock Market Data Dow S And P 500 And Nasdaq For April 23rd
Apr 24, 2025
Latest Posts
-
 Trumps Energy Policy Cheap Oil And Its Geopolitical Implications
May 12, 2025
Trumps Energy Policy Cheap Oil And Its Geopolitical Implications
May 12, 2025 -
 The Impact Of Trumps Presidency On Cheap Oil And The Energy Industry
May 12, 2025
The Impact Of Trumps Presidency On Cheap Oil And The Energy Industry
May 12, 2025 -
 Understanding The Dynamics Between Trumps Policies And Cheap Oil
May 12, 2025
Understanding The Dynamics Between Trumps Policies And Cheap Oil
May 12, 2025 -
 Trumps Cheap Oil Policies An Assessment Of Their Success And Failures
May 12, 2025
Trumps Cheap Oil Policies An Assessment Of Their Success And Failures
May 12, 2025 -
 Examining Trumps Actions And Their Effect On Cheap Oil Production
May 12, 2025
Examining Trumps Actions And Their Effect On Cheap Oil Production
May 12, 2025
