Federal Investigation Reveals Millions Stolen Through Office365 Executive Email Compromise
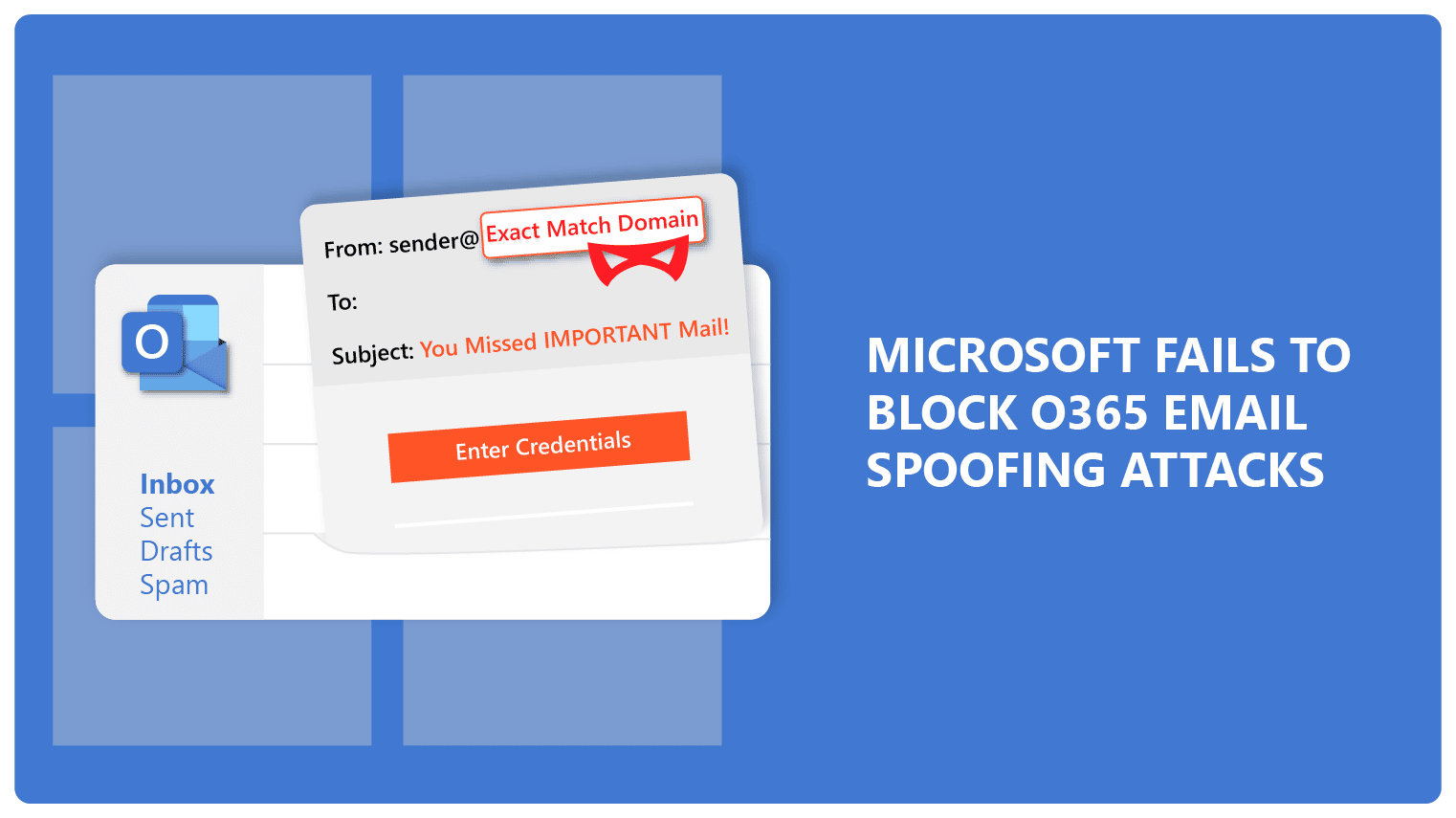
Table of Contents
The Federal Investigation: Scope and Findings
A joint investigation by the FBI's Internet Crime Complaint Center (IC3) and other federal agencies revealed a widespread campaign targeting businesses through Office365 compromise. While specific company names involved often remain confidential due to ongoing investigations, the timeline stretches back several years, illustrating the long-term nature of these sophisticated attacks. The attackers successfully infiltrated numerous organizations, exploiting vulnerabilities in their security protocols to gain access to executive email accounts.
The methods employed were highly effective, relying on a combination of:
- Sophisticated Phishing: Attackers crafted highly realistic phishing emails mimicking legitimate communications from trusted sources, often employing social engineering techniques to manipulate victims into revealing their credentials.
- Credential Stuffing: Attackers utilized stolen credentials obtained from previous data breaches to attempt access to Office365 accounts.
- Exploiting Vulnerabilities: In some cases, attackers exploited known vulnerabilities in outdated software or misconfigured security settings to gain unauthorized access.
The financial losses are staggering, with millions of dollars lost in fraudulent wire transfers. While exact figures are often kept confidential for security and legal reasons, reports suggest losses range from hundreds of thousands to millions of dollars per affected company.
Key Findings of the Federal Investigation:
- Exploited vulnerabilities included weak passwords, lack of MFA, and outdated software versions.
- Phishing techniques involved spear phishing, clone phishing, and whaling attacks.
- The success rate of these attacks was surprisingly high, indicating a need for stronger security measures.
- Stolen funds were laundered through a complex network of international accounts, making tracing and recovery challenging.
How the Office365 Executive Email Compromise Works
The Office365 executive email compromise (EEC) process is insidious and multi-stage. Attackers specifically target high-level executives because they often have the authority to authorize large financial transactions.
The typical process unfolds as follows:
- Targeting Executives: Attackers research target companies and identify high-value executives.
- Sophisticated Phishing: They send highly convincing phishing emails designed to trick executives into revealing their login credentials. This often involves social engineering and impersonating trusted individuals or organizations.
- Credential Acquisition: Once credentials are obtained, attackers access the executive's email account.
- Data Exfiltration: They search for sensitive financial data such as upcoming invoices, payment schedules, and bank account details.
- Fraudulent Transfers: They initiate fraudulent wire transfers, often disguised as legitimate business transactions.
Common Vulnerabilities Exploited in EEC Attacks:
- Weak Passwords: Easily guessed or reused passwords are a prime target for attackers.
- Lack of Multi-Factor Authentication (MFA): The absence of MFA significantly increases the risk of account compromise.
- Poor Security Awareness Training: Employees unaware of phishing techniques are more likely to fall victim.
- Out-of-date Software: Outdated software lacks security patches, creating vulnerabilities that attackers can exploit.
Preventing Office365 Executive Email Compromise
Protecting your business from Office365 executive email compromise requires a multi-layered approach:
- Implement Robust MFA: Mandatory multi-factor authentication for all users is paramount.
- Regular Security Awareness Training: Educate employees on recognizing and reporting phishing attempts.
- Utilize Advanced Threat Protection: Leverage Office365's built-in advanced threat protection features.
- Strong Password Policies: Enforce complex, unique passwords and regular password changes.
- Regular Security Audits: Conduct periodic security assessments to identify and address vulnerabilities.
- Simulated Phishing Attacks: Test employee awareness and preparedness with simulated phishing exercises.
Preventative Measures Summary:
- Implement advanced email security solutions like email authentication (SPF, DKIM, DMARC) and anti-phishing filters.
- Regularly conduct security audits to identify weaknesses in your security posture.
- Invest in comprehensive employee training programs focused on phishing and social engineering tactics.
The Role of Multi-Factor Authentication (MFA)
MFA is a critical component of any effective cybersecurity strategy. It adds an extra layer of security by requiring multiple forms of authentication, such as a password and a code from a mobile app, before granting access to an account. This makes it exponentially more difficult for attackers to gain unauthorized access, even if they have obtained the user's password. Consider implementing different MFA options, like time-based one-time passwords (TOTP), push notifications, or hardware security keys, to suit your business needs.
The Importance of Security Awareness Training
Educating employees is crucial in preventing phishing attacks. Regular security awareness training programs should equip employees with the knowledge to identify and report suspicious emails. Training should cover various phishing techniques, including spear phishing and clone phishing, and should emphasize the importance of verifying the sender's identity before clicking links or opening attachments. Regular training, including simulated phishing campaigns, helps to build a strong security culture within the organization.
Conclusion: Protecting Your Business from Office365 Executive Email Compromise
The federal investigation highlights the severity of Office365 executive email compromise and the devastating financial consequences it can have for businesses. The millions lost underscore the urgent need for robust security measures. By implementing multi-factor authentication, providing comprehensive security awareness training, and utilizing advanced threat protection tools, organizations can significantly reduce their risk of falling victim to these attacks. Don't become another victim of an Office365 executive email compromise. Implement robust security protocols today to safeguard your organization's financial assets and reputation. For more information on implementing MFA and security awareness training, [link to relevant resource 1] and [link to relevant resource 2].

Featured Posts
-
 Saturday Lotto Results April 12th Check The Jackpot Numbers
May 07, 2025
Saturday Lotto Results April 12th Check The Jackpot Numbers
May 07, 2025 -
 What Happens In A Conclave The Election Of The Pope Explained
May 07, 2025
What Happens In A Conclave The Election Of The Pope Explained
May 07, 2025 -
 Cool Girl Rihanna New Engagement Ring And Chic Red Heels
May 07, 2025
Cool Girl Rihanna New Engagement Ring And Chic Red Heels
May 07, 2025 -
 Las Vegas Aces And Dallas Wings To Play Preseason Game At Notre Dame
May 07, 2025
Las Vegas Aces And Dallas Wings To Play Preseason Game At Notre Dame
May 07, 2025 -
 Lewis Capaldis Music Comeback New Studio Plans Confirm Return
May 07, 2025
Lewis Capaldis Music Comeback New Studio Plans Confirm Return
May 07, 2025
Latest Posts
-
 Building A Resilient Future The Third Ldc Future Forums Action Plan
May 07, 2025
Building A Resilient Future The Third Ldc Future Forums Action Plan
May 07, 2025 -
 Resilience In Least Developed Countries Key Outcomes From The Third Ldc Future Forum
May 07, 2025
Resilience In Least Developed Countries Key Outcomes From The Third Ldc Future Forum
May 07, 2025 -
 Governments Plan For A Successful Ldc Graduation
May 07, 2025
Governments Plan For A Successful Ldc Graduation
May 07, 2025 -
 Minister Tavio To Visit Zambia And Attend The Least Developed Countries Ldc Future Forum An Apo Group Press Release
May 07, 2025
Minister Tavio To Visit Zambia And Attend The Least Developed Countries Ldc Future Forum An Apo Group Press Release
May 07, 2025 -
 Ldc Future Forum Concludes Ambitious Plans For Resilience
May 07, 2025
Ldc Future Forum Concludes Ambitious Plans For Resilience
May 07, 2025
