Innovative Block Mirror Techniques: A Dystopian Site's Response To Censorship

Table of Contents
Understanding the Need for Block Mirror Techniques
Censorship's impact on online freedom is profound, stifling open dialogue and limiting access to crucial information. The need for circumvention strategies like Block Mirror Techniques is driven by several factors:
- Increased government surveillance and internet control: Many governments actively monitor and control internet access, restricting access to specific websites and information sources.
- Geo-blocking and content restrictions: Websites are often blocked based on geographical location, preventing users in certain regions from accessing content.
- The suppression of dissenting voices and information: Censorship is frequently used to silence opposition and control the narrative, hindering the free exchange of ideas.
- The rise of sophisticated censorship techniques: Traditional methods of censorship are becoming increasingly sophisticated, requiring more advanced circumvention strategies.
Traditional methods like VPNs and proxies, while helpful, are becoming increasingly ineffective against sophisticated censorship techniques implemented by authoritarian regimes and corporations alike. These more advanced methods often employ deep packet inspection and other technologies capable of identifying and blocking VPN traffic. The need for robust censorship circumvention strategies and the protection of internet freedom and digital rights is paramount in this increasingly restrictive digital landscape.
Types of Innovative Block Mirror Techniques
The development of Block Mirror Techniques has become increasingly sophisticated in response to the rise in sophisticated censorship. Several innovative approaches are employed to bypass these restrictions:
Decentralized Networks
Decentralized networks like IPFS (InterPlanetary File System) and blockchain technologies offer a powerful solution to censorship. By distributing mirrored content across a vast network of nodes, these techniques make it extremely difficult to take down the entire site.
- Increased resilience against takedown attempts: Taking down a single node does not affect the availability of the content, as it's mirrored across countless others.
- Difficulty in identifying and blocking all nodes: The distributed nature makes it computationally expensive and practically impossible to identify and block every node in the network.
- Enhanced security and anonymity for users: Decentralized networks often provide greater anonymity and security for users accessing the mirrored content.
Keywords like "IPFS mirroring," "blockchain censorship resistance," and "decentralized web" highlight the core principles of this approach.
Dynamic Domain Name System (DNS) Techniques
Dynamic DNS and domain fronting are used to mask the true location of mirrored content, making it difficult for censors to pinpoint and block the site.
- Constant shifting of domain names: The website's address constantly changes, making it hard for censors to maintain a consistent block.
- Makes it difficult to track and block content consistently: The dynamic nature of the system makes it a moving target for censorship efforts.
- Requires sophisticated infrastructure management: Maintaining a dynamic DNS system requires substantial technical expertise and infrastructure.
Related keywords like "DNSSEC," "domain fronting," and "anonymous DNS" underscore the technical complexities involved.
Content Obfuscation and Encryption
Encryption and steganography—the art of hiding information within other information—are crucial components of many Block Mirror Techniques. These methods conceal the content, making it much more challenging for censors to identify and block.
- Makes it more difficult for censors to identify and block the content: Encrypted content is unintelligible to censors without the decryption key.
- Adds another layer of security for users and the content itself: Encryption safeguards both the users' privacy and the integrity of the information.
- Requires specialized software and understanding of cryptographic techniques: Implementing effective encryption requires specialized knowledge and tools.
Keywords such as "data encryption," "steganography," and "secure communication" reflect the security-focused nature of these techniques.
The Cat and Mouse Game: The Ongoing Evolution of Block Mirror Techniques and Censorship
The development of Block Mirror Techniques is a continuous arms race against increasingly sophisticated censorship technologies. Both sides are constantly adapting and evolving their strategies.
- The arms race between developers and censors: As censors develop new methods of blocking access, developers create new circumvention techniques.
- The need for constant innovation in circumvention strategies: Staying ahead of the curve requires continuous research, development, and adaptation.
- The challenges of staying ahead of increasingly sophisticated censorship technologies: This ongoing struggle highlights the complex challenges in maintaining internet freedom.
Keywords like "digital security," "cybersecurity," and "internet governance" emphasize the broader context of this technological battle.
Conclusion
The fight for free information in the face of escalating censorship necessitates innovative solutions. Block Mirror Techniques, encompassing decentralized networks, dynamic DNS, and content obfuscation, represent a crucial element in this fight. While the battle between censorship and circumvention remains ongoing, the ingenuity and persistence of those seeking to preserve online freedom continue to push the boundaries of what’s possible. Learning about and understanding these Block Mirror Techniques is essential for navigating the complexities of the digital world and ensuring access to information remains a fundamental right. Stay informed about the latest advancements in block mirror technologies to safeguard your digital freedom.

Featured Posts
-
 Los Angeles Dodgers Left Handed Bats Aim For A Turnaround
May 16, 2025
Los Angeles Dodgers Left Handed Bats Aim For A Turnaround
May 16, 2025 -
 Kid Cudi Auction High Prices For Jewelry And Sneakers
May 16, 2025
Kid Cudi Auction High Prices For Jewelry And Sneakers
May 16, 2025 -
 La Liga Extends Reach With Multi Year Fan Code Partnership
May 16, 2025
La Liga Extends Reach With Multi Year Fan Code Partnership
May 16, 2025 -
 En Directo Venezia Napoles
May 16, 2025
En Directo Venezia Napoles
May 16, 2025 -
 Neal Pionk Updates Recent News And Highlights
May 16, 2025
Neal Pionk Updates Recent News And Highlights
May 16, 2025
Latest Posts
-
 Diddy Trial Update Cassie Ventura Grilled On Relationship With Sean Combs
May 17, 2025
Diddy Trial Update Cassie Ventura Grilled On Relationship With Sean Combs
May 17, 2025 -
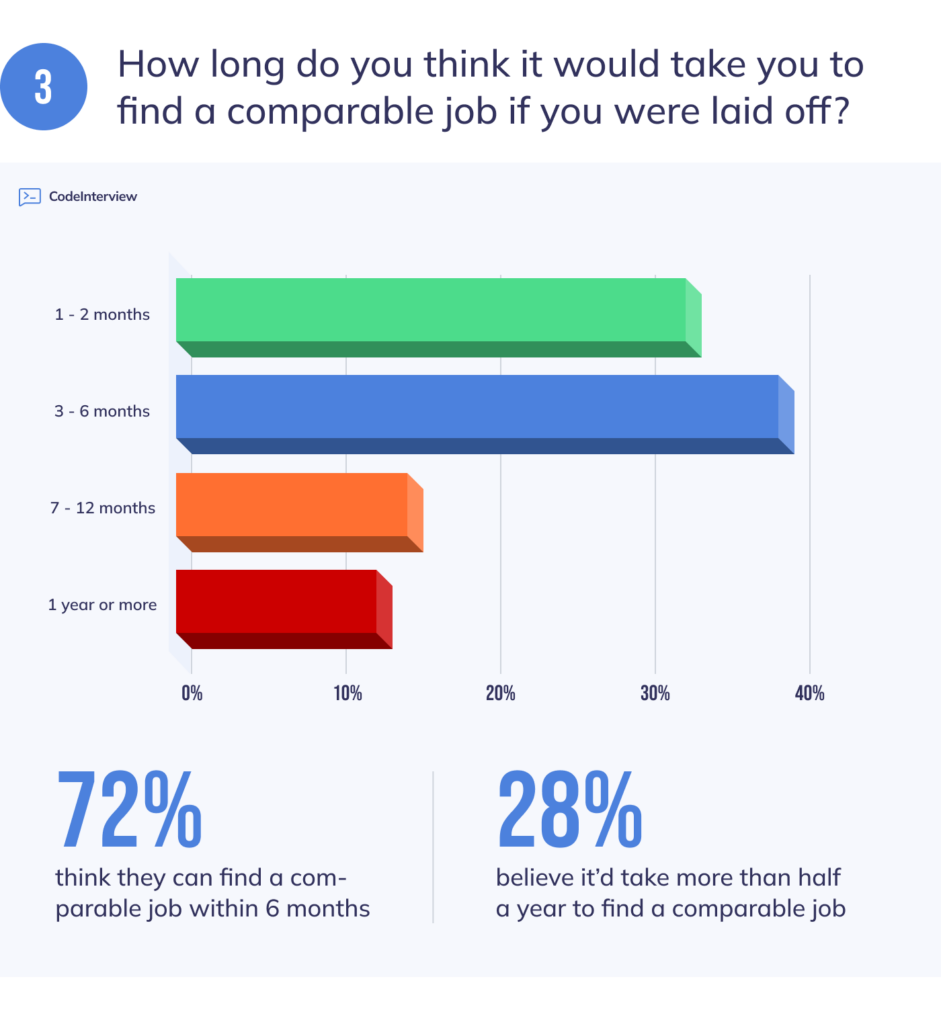 Is Your Salary Too High For The Current Job Market Strategies For Finding A New Role
May 17, 2025
Is Your Salary Too High For The Current Job Market Strategies For Finding A New Role
May 17, 2025 -
 Covid 19 Vaccine Policy Change Proposed Rfk Jr S Hhs To Reconsider Routine Vaccinations
May 17, 2025
Covid 19 Vaccine Policy Change Proposed Rfk Jr S Hhs To Reconsider Routine Vaccinations
May 17, 2025 -
 Market Chaos The Ultra Wealthy Find Stability In Luxury Real Estate
May 17, 2025
Market Chaos The Ultra Wealthy Find Stability In Luxury Real Estate
May 17, 2025 -
 Trumps Foreign Policy And His Interactions With Arab Leaders
May 17, 2025
Trumps Foreign Policy And His Interactions With Arab Leaders
May 17, 2025
