Massive Office365 Data Breach Nets Hacker Millions, Authorities Reveal
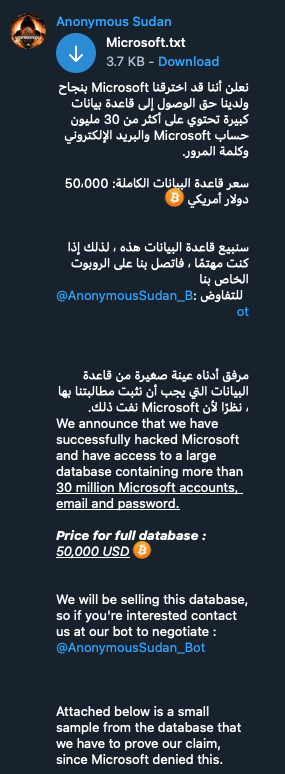
Table of Contents
The Scale and Impact of the Office365 Data Breach
While the exact number of victims remains under investigation, preliminary reports suggest thousands of users across North America and Europe were affected by this sophisticated Office365 data breach. The compromised data included a range of sensitive information:
- Emails and email attachments: Hackers gained access to countless emails, potentially exposing confidential business communications, personal correspondence, and sensitive attachments.
- Financial records: The breach exposed financial records, including bank account details, credit card information, and invoices, leading to potential financial fraud and identity theft.
- Customer data: Customer lists, personal details, and purchase histories were compromised, putting businesses at risk of regulatory penalties and reputational damage.
- Intellectual property: The theft of intellectual property, such as trade secrets, research data, and proprietary software, poses a significant threat to the competitiveness of affected businesses.
- Employee information: Access to employee data, including social security numbers, addresses, and salary information, increases the risk of identity theft and other forms of exploitation.
The financial losses for affected businesses and individuals could be staggering. Beyond direct financial theft, businesses face potential legal fees, reputational damage, and the cost of recovering from the breach. Individuals face the risk of identity theft, credit card fraud, and other forms of financial exploitation. Furthermore, some victims reported subsequent ransomware attacks, further exacerbating the damage caused by the initial breach.
How the Hackers Achieved Access: Exploiting Office365 Vulnerabilities
The hackers employed a multi-pronged approach to gain access to Office365 accounts. Investigations suggest a combination of techniques:
- Sophisticated phishing campaigns: Hackers sent highly convincing phishing emails designed to trick users into revealing their login credentials. These emails often mimicked legitimate communications from trusted sources.
- Credential stuffing: The hackers used stolen credentials obtained from previous data breaches to attempt to access Office365 accounts.
- Exploiting zero-day vulnerabilities: While the specific vulnerabilities exploited are still under investigation, the breach highlights the ever-present danger of unknown security flaws in software.
Examples of Phishing Emails:
- Emails appearing to be from Microsoft, requesting password resets.
- Emails containing malicious links disguised as legitimate Office365 documents.
- Emails offering enticing deals or promotions, leading to compromised websites.
Common Vulnerabilities in Office 365 Applications:
- Weak or reused passwords
- Lack of multi-factor authentication (MFA)
- Outdated software and unpatched security flaws
The importance of strong passwords, incorporating multi-factor authentication (MFA), and staying current with software updates and patches cannot be overstated. These simple yet crucial steps significantly reduce the likelihood of successful breaches.
The Authorities' Response and Ongoing Investigation
Several authorities, including the FBI and national cybersecurity agencies, are involved in the ongoing investigation. Their actions include:
- Working to identify and apprehend the perpetrators.
- Collaborating with affected organizations to mitigate the damage.
- Issuing cybersecurity alerts and advisories to warn of similar threats.
Legal repercussions and charges are anticipated as the investigation progresses. The ongoing nature of the investigation means further updates and related cybersecurity alerts are likely in the coming weeks and months.
Protecting Your Business from Similar Office365 Data Breaches
Strengthening your Office365 security is paramount. Consider implementing the following:
- Robust Multi-Factor Authentication (MFA): MFA adds an extra layer of security, making it significantly harder for hackers to access accounts even if they obtain passwords.
- Regular Security Audits and Penetration Testing: Regular assessments identify vulnerabilities before they can be exploited.
- Employee Security Awareness Training: Educate employees about phishing scams, social engineering tactics, and secure password practices.
- Data Encryption and Loss Prevention Measures: Encrypt sensitive data both at rest and in transit to prevent unauthorized access.
- Regular Software Updates and Patching: Stay up-to-date with the latest security patches to address known vulnerabilities.
Using reputable security solutions compatible with Office365 and adopting best practices for password management are equally crucial.
Conclusion: Learning from the Massive Office365 Data Breach
This massive Office365 data breach serves as a stark reminder of the ever-present threat of cyberattacks. The scale of the impact and the sophisticated methods employed by the hackers highlight the critical need for proactive security measures. By implementing robust security protocols, including MFA, regular security audits, employee training, and data encryption, businesses and individuals can significantly reduce their risk. Review your Office365 security protocols today. Preventing Office365 breaches requires vigilance and a multi-layered approach to security. Securing your Office365 data is not just a best practice; it's a necessity in today's digital landscape. Implement Office365 security best practices now to protect your valuable information.

Featured Posts
-
 How Stefano Domenicali Transformed Formula 1s Global Presence
May 04, 2025
How Stefano Domenicali Transformed Formula 1s Global Presence
May 04, 2025 -
 Anna Kendricks Crucial Role In The Accountant 3 Why The Accountant 2 Proves It
May 04, 2025
Anna Kendricks Crucial Role In The Accountant 3 Why The Accountant 2 Proves It
May 04, 2025 -
 Bob Bafferts Kentucky Derby Return An Identity Crisis In Racing
May 04, 2025
Bob Bafferts Kentucky Derby Return An Identity Crisis In Racing
May 04, 2025 -
 Utrecht Wastewater Plant Netherlands Largest Heat Pump Launched
May 04, 2025
Utrecht Wastewater Plant Netherlands Largest Heat Pump Launched
May 04, 2025 -
 Wildfire Speculation Examining The Risks Of Betting On Las Fires
May 04, 2025
Wildfire Speculation Examining The Risks Of Betting On Las Fires
May 04, 2025
Latest Posts
-
 A Timeline Of The Alleged Disagreement Between Blake Lively And Anna Kendrick
May 04, 2025
A Timeline Of The Alleged Disagreement Between Blake Lively And Anna Kendrick
May 04, 2025 -
 Decoding Anna Kendricks Body Language A Blake Lively Interview Analysis
May 04, 2025
Decoding Anna Kendricks Body Language A Blake Lively Interview Analysis
May 04, 2025 -
 The Reported Feud Between Blake Lively And Anna Kendrick A Detailed Timeline
May 04, 2025
The Reported Feud Between Blake Lively And Anna Kendrick A Detailed Timeline
May 04, 2025 -
 Blake Lively And Anna Kendricks Relationship A Timeline Of Events
May 04, 2025
Blake Lively And Anna Kendricks Relationship A Timeline Of Events
May 04, 2025 -
 Anna Kendrick Mum On Blake Lively Legal Dispute At Movie Premiere
May 04, 2025
Anna Kendrick Mum On Blake Lively Legal Dispute At Movie Premiere
May 04, 2025
