Millions In Losses: FBI Probes Executive Office365 Data Breach
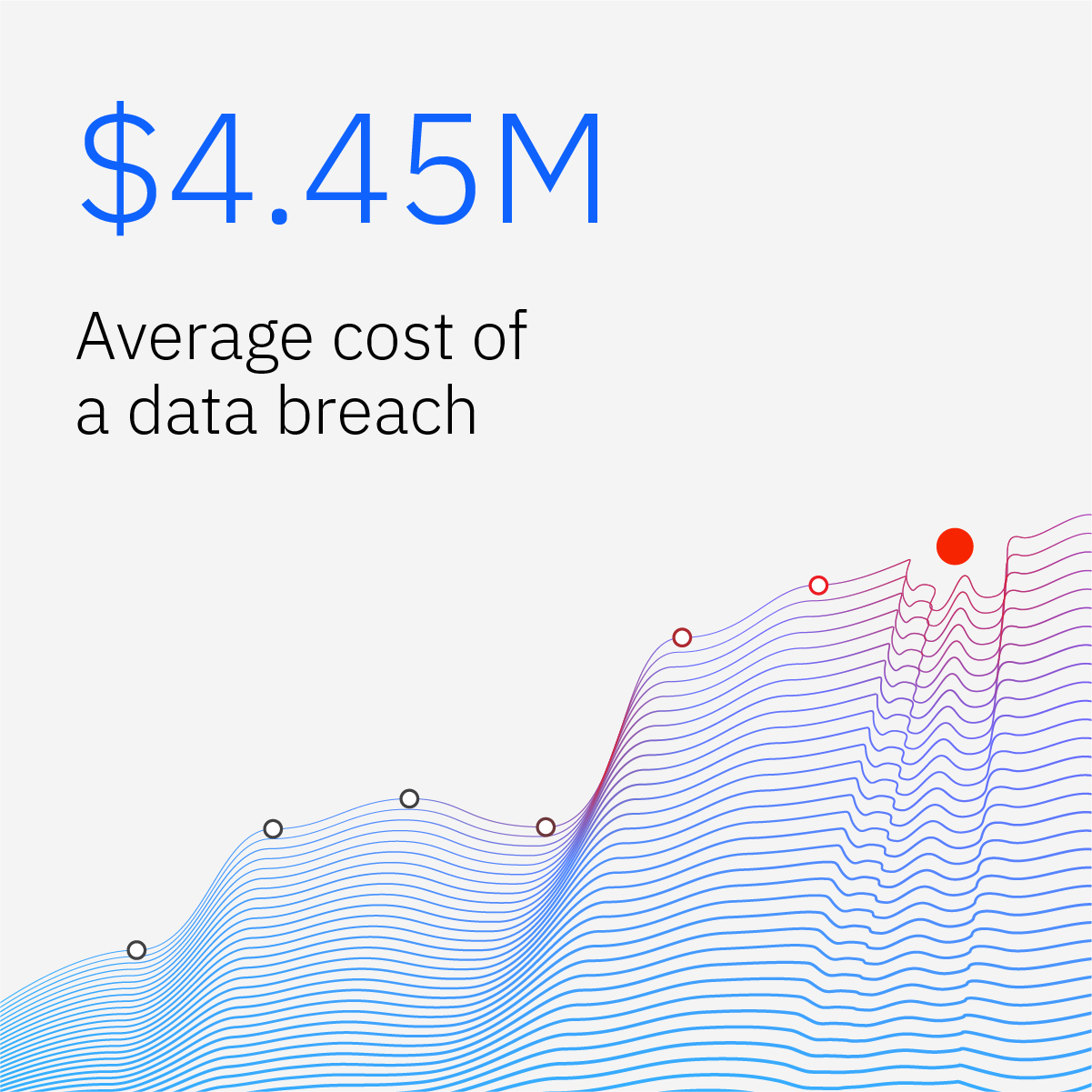
Table of Contents
H2: The Scale of the Office365 Data Breach and its Financial Impact
The extent of this Office365 data breach is currently under investigation, but early reports indicate a significant number of executive accounts were compromised. The types of data compromised are believed to include sensitive financial records, intellectual property, and confidential customer data. The financial impact is staggering, with estimates placing the losses in the millions of dollars. This figure doesn't just encompass the direct financial losses; it also includes potential legal fees, reputational damage, and the disruption of business operations. The long-term consequences could be even more severe, potentially impacting investor confidence and market share.
- Estimated financial loss: Millions of dollars, with ongoing assessments underway.
- Types of sensitive data compromised: Financial records, intellectual property, customer data, and potentially employee personal information.
- Potential long-term financial consequences: Loss of investor confidence, decreased market share, significant legal expenses, and damage to brand reputation.
H2: FBI Investigation: Key Focus Areas and Potential Charges
The FBI's investigation into this Office365 data breach is ongoing, focusing on identifying the perpetrators and determining the methods used to gain unauthorized access. Investigators are likely pursuing multiple lines of inquiry, examining network logs, compromised accounts, and potentially interviewing individuals with access to the affected systems. Potential charges against those responsible could include identity theft, wire fraud, and violations of various data security laws, depending on the evidence gathered. The severity of the charges will depend on the extent of the damage and the intent of the perpetrators.
- The FBI's current investigative stage: Active investigation, focusing on identifying perpetrators and methods.
- Potential legal ramifications for perpetrators: Significant prison time and substantial fines under various federal laws.
- Types of charges being considered: Identity theft, wire fraud, Computer Fraud and Abuse Act violations, and potential state-level charges.
H2: Vulnerabilities Exploited in the Office365 Data Breach and Prevention Strategies
While the specific vulnerabilities exploited in this Executive Office365 data breach remain undisclosed, several common weaknesses could have been targeted. These include phishing attacks designed to trick users into revealing their credentials, weak or reused passwords, unpatched software vulnerabilities in Office365 applications, and potentially insider threats. Preventing similar Office365 data breaches requires a multi-layered approach.
- Common vulnerabilities in Office365: Phishing attacks, weak passwords, outdated software, and insufficient multi-factor authentication.
- Best practices for securing Office365 accounts and data: Implement multi-factor authentication (MFA), enforce strong password policies, conduct regular security awareness training for employees, and keep all software updated.
- Importance of multi-factor authentication (MFA), security awareness training, regular software updates: MFA adds an extra layer of security, training helps employees identify phishing attempts, and regular updates patch vulnerabilities.
H2: The Long-Term Implications for Cybersecurity and Data Protection
This Office365 data breach highlights the increasing sophistication of cyberattacks and the growing need for robust cybersecurity measures. The incident could also lead to increased regulatory scrutiny and potential changes to data protection laws, pushing businesses to adopt more stringent security practices. The impact on public trust is also significant, potentially impacting consumer confidence and willingness to share data with affected organizations.
- The evolving threat landscape for cyberattacks: Cyberattacks are becoming more frequent, sophisticated, and targeted.
- The importance of proactive cybersecurity measures: Proactive measures are crucial to mitigate risks and protect against future breaches.
- The role of government regulations in data protection: Governments are increasingly enacting stricter regulations to protect sensitive data.
3. Conclusion:
The FBI's investigation into this Executive Office365 data breach underscores the severe financial and reputational consequences of inadequate cybersecurity. Millions of dollars in losses highlight the critical need for robust security practices. The breach exposes vulnerabilities in commonly used platforms and emphasizes the importance of proactive measures like multi-factor authentication, employee training, and regular software updates. Protect your business from an Office365 data breach – implement robust security measures today! Learn more about securing your Office365 environment and preventing costly data breaches by researching best practices and investing in appropriate security solutions.

Featured Posts
-
 How Middle Managers Drive Company Productivity And Employee Engagement
May 05, 2025
How Middle Managers Drive Company Productivity And Employee Engagement
May 05, 2025 -
 Volkanovski Vs Lopes Ufc 314 A Comprehensive Review Of Winners And Losers
May 05, 2025
Volkanovski Vs Lopes Ufc 314 A Comprehensive Review Of Winners And Losers
May 05, 2025 -
 Bookstores Valuable Find A 45 000 Rare Novel
May 05, 2025
Bookstores Valuable Find A 45 000 Rare Novel
May 05, 2025 -
 A Critical Assessment Of Marvels Current Cinematic And Television Output
May 05, 2025
A Critical Assessment Of Marvels Current Cinematic And Television Output
May 05, 2025 -
 March Heatwave Alert Kolkata Temperature Forecast
May 05, 2025
March Heatwave Alert Kolkata Temperature Forecast
May 05, 2025
Latest Posts
-
 Ufc 314 Co Main Event Expert Predictions For Chandler Vs Pimblett
May 05, 2025
Ufc 314 Co Main Event Expert Predictions For Chandler Vs Pimblett
May 05, 2025 -
 Bryce Mitchell And Jean Silvas Ufc 314 Press Conference A Heated Confrontation
May 05, 2025
Bryce Mitchell And Jean Silvas Ufc 314 Press Conference A Heated Confrontation
May 05, 2025 -
 Analyzing The Odds A Prediction For Ufc 314s Chandler Vs Pimblett
May 05, 2025
Analyzing The Odds A Prediction For Ufc 314s Chandler Vs Pimblett
May 05, 2025 -
 Mitchell Vs Silva Heated Exchange At Ufc 314 Press Conference Leads To Accusation
May 05, 2025
Mitchell Vs Silva Heated Exchange At Ufc 314 Press Conference Leads To Accusation
May 05, 2025 -
 Ufc 314 In Depth Look At Chandler Vs Pimblett Odds And Predictions
May 05, 2025
Ufc 314 In Depth Look At Chandler Vs Pimblett Odds And Predictions
May 05, 2025
