Millions Made From Office365 Breaches: Inside The Executive Email Heist
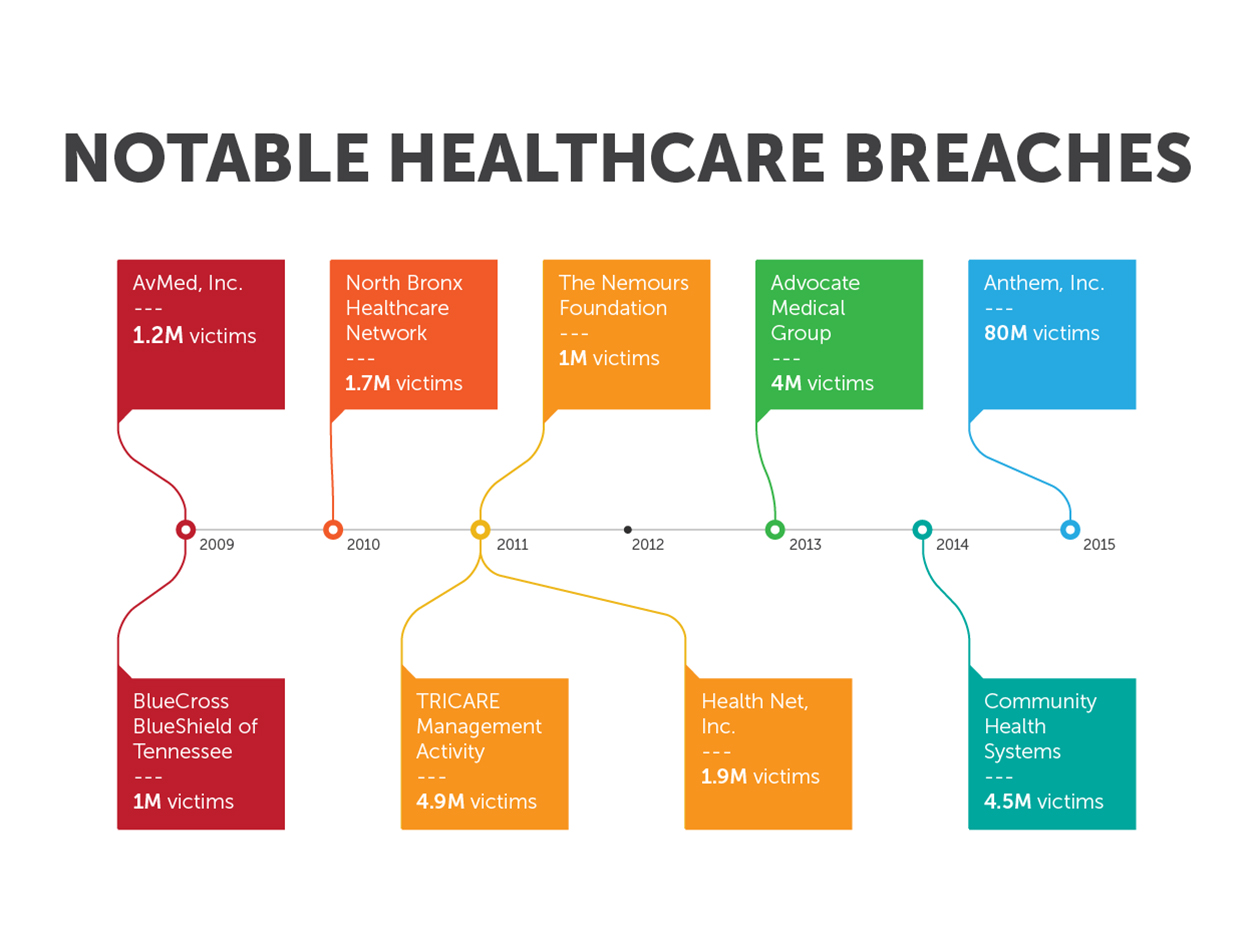
Table of Contents
The Anatomy of an Executive Email Heist
Executive email heists are complex operations, often involving a multi-stage attack leveraging various techniques. Understanding these methods is the first step towards effective prevention.
Phishing and Spear Phishing Attacks
Phishing and spear phishing are the most common entry points for these attacks. Attackers craft highly personalized emails mimicking legitimate communications from trusted sources, often employing Microsoft branding to increase credibility. These emails may contain malicious links or attachments designed to deliver malware or steal credentials.
- Spear-phishing techniques: Emails impersonating colleagues, board members, or even clients, often containing urgent requests or sensitive information.
- Social engineering tactics: Manipulating recipients into divulging confidential information or clicking malicious links through emotional appeals, urgency, and authority.
- Successful attack vectors: Exploiting known vulnerabilities in Office365 applications, leveraging compromised email accounts, and using malicious macros in Word or Excel documents.
- Statistics show that a significant percentage of successful phishing attacks target executives, highlighting their vulnerability to these sophisticated tactics.
Exploiting Weak Passwords and MFA Bypass
Even with sophisticated phishing defenses, weak passwords and bypassed multi-factor authentication (MFA) remain significant vulnerabilities. Attackers often leverage stolen credentials obtained through phishing or other methods to gain unauthorized access.
- Common password vulnerabilities: Reusing passwords across multiple accounts, using easily guessable passwords, and failing to implement strong password policies.
- MFA bypass techniques: Using brute-force attacks, exploiting vulnerabilities in MFA implementations, or using social engineering to trick users into revealing their MFA codes.
- Importance of strong password management: Implementing strong, unique passwords for each account and using a reputable password manager significantly reduces the risk of credential compromise.
The Role of Malware and Ransomware
Once initial access is gained, attackers often deploy malware to further compromise systems and steal data. Ransomware is frequently used to extort funds or prevent data recovery.
- Examples of malware used in Office365 breaches: Keyloggers, remote access Trojans (RATs), and various forms of data exfiltration malware.
- Common ransomware demands: Large sums of money in exchange for decrypting files or preventing data release.
- Impact on business operations: Disruption of critical business processes, loss of productivity, financial losses, legal and regulatory repercussions, and reputational damage.
The Financial Ramifications of Office365 Breaches
The financial consequences of successful Office365 breaches targeting executives can be devastating, far exceeding the costs associated with other types of cyberattacks.
The High Cost of Executive-Level Compromises
Executive-level compromises often result in significant financial losses due to the high value of transactions they oversee. CEO fraud and wire transfer fraud are common outcomes, leading to substantial losses.
- Examples of large-scale financial losses: Numerous real-world cases demonstrate the potential for millions of dollars in losses from successful executive email heists.
- Statistics highlight the average cost of data breaches and recovery, emphasizing the significant financial burden on organizations.
Reputational Damage and Loss of Trust
Beyond the direct financial losses, successful breaches inflict severe reputational damage. Loss of customer trust, investor confidence, and potential legal repercussions can have long-term consequences.
- Negative consequences of a public breach: Negative media coverage, loss of market share, damaged customer relationships, and potential legal action.
- Potential lawsuits: Organizations can face lawsuits from customers, investors, and regulatory bodies following a breach.
- Damage to investor confidence: A security breach can significantly impact a company's stock price and investor confidence.
Protecting Your Organization from Office365 Breaches
Proactive security measures are crucial for preventing executive email heists and mitigating their devastating effects.
Implementing Robust Security Measures
Strengthening your organization's security posture is paramount. This involves a multi-layered approach.
- Strong password policies: Enforce complex, unique passwords and regular password changes.
- Multi-factor authentication (MFA): Implement MFA for all Office365 accounts, requiring multiple verification factors for login.
- Employee training: Conduct regular cybersecurity awareness training to educate employees about phishing scams and social engineering tactics.
- Regular security audits: Perform regular security assessments to identify vulnerabilities and ensure security controls are effective.
- Advanced threat protection: Utilize advanced threat protection features within Office365 to detect and block malicious emails and attachments.
- Email authentication protocols: Implement DMARC, SPF, and DKIM to verify the authenticity of emails and prevent spoofing.
Investing in Cybersecurity Awareness Training
Investing in comprehensive cybersecurity awareness training is crucial. Employees are often the weakest link in the security chain.
- Training program recommendations: Implement regular, engaging training programs that cover various aspects of cybersecurity, including phishing awareness, password management, and social engineering.
- Regular phishing simulations: Conduct simulated phishing attacks to test employee awareness and reinforce training.
- Benefits of ongoing security awareness education: Continuous education helps maintain a high level of awareness and improves the organization's overall security posture.
Conclusion
Office365 breaches targeting executives represent a significant financial and reputational risk to organizations. The high cost of these attacks, coupled with the potential for irreparable reputational damage, underscores the urgent need for proactive security measures. Don't let your organization become the next victim of an Office365 breach. Take control of your security today by implementing robust security measures, investing in comprehensive employee training programs, and staying vigilant against evolving cyber threats. Learn more about protecting yourself from executive email heists and build a resilient security posture for your organization.

Featured Posts
-
 Chris Pratts Unfiltered Opinion On Patrick Schwarzeneggers White Lotus Appearance
May 06, 2025
Chris Pratts Unfiltered Opinion On Patrick Schwarzeneggers White Lotus Appearance
May 06, 2025 -
 Schwarzenegger Joins Guadagninos Film A Prominent New Role
May 06, 2025
Schwarzenegger Joins Guadagninos Film A Prominent New Role
May 06, 2025 -
 Patrick Schwarzeneggers Nude Scenes Father Arnolds View
May 06, 2025
Patrick Schwarzeneggers Nude Scenes Father Arnolds View
May 06, 2025 -
 Patrick Schwarzeneggers Wedding Delay The Reason Behind The Postponement
May 06, 2025
Patrick Schwarzeneggers Wedding Delay The Reason Behind The Postponement
May 06, 2025 -
 Stock Market Defies Recession Fears Investors See Continued Growth
May 06, 2025
Stock Market Defies Recession Fears Investors See Continued Growth
May 06, 2025
Latest Posts
-
 Sabrina Carpenters Virtual Fortnite Concert Date Time And Details
May 06, 2025
Sabrina Carpenters Virtual Fortnite Concert Date Time And Details
May 06, 2025 -
 Fortnite Festival Sabrina Carpenters Virtual Performance Announced
May 06, 2025
Fortnite Festival Sabrina Carpenters Virtual Performance Announced
May 06, 2025 -
 I Dont Know Why I Just Do Jeff Goldblum Ariana Grande And The Mildred Snitzer Orchestra Collaboration
May 06, 2025
I Dont Know Why I Just Do Jeff Goldblum Ariana Grande And The Mildred Snitzer Orchestra Collaboration
May 06, 2025 -
 Sabrina Carpenter To Headline Fortnite Virtual Festival Fans React
May 06, 2025
Sabrina Carpenter To Headline Fortnite Virtual Festival Fans React
May 06, 2025 -
 Jeff Goldblum And The Mildred Snitzer Orchestras I Dont Know Why I Just Do Ft Ariana Grande A Musical Collaboration
May 06, 2025
Jeff Goldblum And The Mildred Snitzer Orchestras I Dont Know Why I Just Do Ft Ariana Grande A Musical Collaboration
May 06, 2025
