Office365 Executive Inboxes Targeted In Multi-Million Dollar Cybercrime
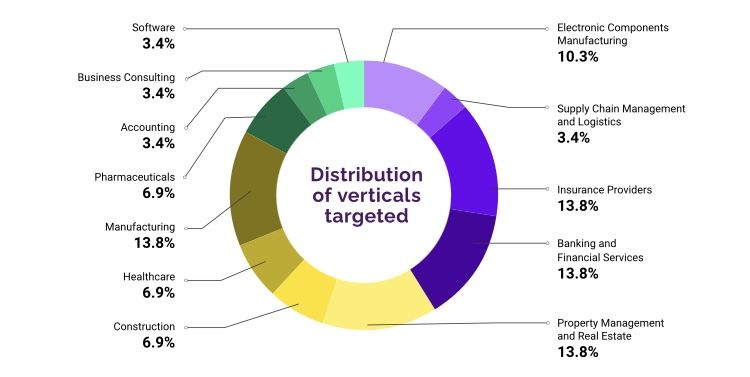
Table of Contents
The Growing Threat of Targeted Office365 Attacks
The vulnerability of Office365 executive inboxes stems from a convergence of factors, making them prime targets for cybercriminals. Understanding these threats is the first step toward effective protection.
Sophisticated Phishing and Spear Phishing Campaigns
Attackers employ increasingly sophisticated phishing and spear phishing techniques to gain access to executive accounts. These campaigns often involve:
- Personalized phishing emails: Emails tailored to the recipient's job title, company, and even personal details, making them appear authentic.
- Exploiting known vulnerabilities: Attackers leverage zero-day exploits and known vulnerabilities in Office365 to bypass security measures.
- Use of malware: Malicious attachments or links within emails deliver malware, such as ransomware or keyloggers, to steal credentials or encrypt sensitive data.
Attackers meticulously craft these emails to bypass spam filters and security software. They may use legitimate-looking domains or impersonate trusted individuals within the organization to increase credibility and trick unsuspecting victims into clicking malicious links or opening infected attachments.
Exploiting Weak Security Practices
Many organizations unknowingly create vulnerabilities that make them easy targets for attackers. Common weaknesses include:
- Lack of multi-factor authentication (MFA): MFA adds an extra layer of security, significantly reducing the risk of unauthorized access even if credentials are compromised.
- Outdated software: Failing to update software leaves systems vulnerable to known exploits.
- Insufficient security awareness training: Employees unaware of phishing tactics are more likely to fall victim to attacks.
Neglecting these basic security measures creates significant entry points for attackers, making it easier for them to compromise Office365 executive inboxes and gain access to sensitive information.
The High Value of Executive Accounts
Executives represent the ultimate prize for cybercriminals. Their accounts grant access to:
- Financial data: Bank accounts, investment information, and other sensitive financial records.
- Intellectual property: Trade secrets, strategic plans, and confidential business information.
- Business disruption: Access to critical systems can disrupt operations and cause significant financial losses.
The potential financial losses associated with a compromised executive account are immense, making them highly attractive targets for sophisticated cyberattacks. A single successful attack can cost millions in direct and indirect costs.
Understanding the Financial Impact of Office365 Breaches
The financial consequences of a successful Office365 breach extend far beyond the initial compromise.
Direct Financial Losses
Direct costs associated with Office365 breaches can be crippling:
- Ransomware attacks: Organizations may be forced to pay substantial ransoms to regain access to their encrypted data.
- Regulatory fines: Non-compliance with regulations like GDPR and CCPA can result in hefty fines.
- Lost revenue: Disruption to operations and loss of customer trust can significantly impact revenue streams.
Real-world examples demonstrate the devastating financial impact. Numerous cases highlight multi-million dollar losses due to ransomware attacks alone.
Indirect Costs
Beyond the immediate financial losses, indirect costs can have a long-term detrimental effect:
- Reputational damage: A data breach can severely damage an organization's reputation, impacting customer loyalty and investor confidence.
- Loss of investor confidence: News of a security breach can lead to a decline in stock prices and make it difficult to secure future investments.
- Decreased productivity: The time and resources spent on investigating and remediating a breach significantly reduce productivity.
These indirect costs often outweigh the direct financial losses, highlighting the importance of robust security measures.
Protecting Your Office365 Executive Inboxes
Protecting your Office365 executive inboxes requires a multi-layered approach combining proactive security measures and advanced security solutions.
Implementing Robust Security Measures
Strengthening your security posture begins with implementing fundamental security best practices:
- Multi-factor authentication (MFA): Enable MFA for all executive accounts to add an extra layer of security.
- Advanced threat protection: Leverage Office365's built-in advanced threat protection features to detect and block malicious emails and attachments.
- Security awareness training: Regularly train employees on phishing recognition and safe email practices.
These measures significantly reduce the risk of successful attacks, forming the bedrock of a strong security posture.
Utilizing Advanced Security Solutions
Investing in advanced security solutions further enhances your protection:
- Email security gateways: Deploy email security gateways to filter malicious emails and attachments before they reach inboxes.
- Data loss prevention (DLP) solutions: Implement DLP solutions to prevent sensitive data from leaving the organization's network.
- Security information and event management (SIEM) systems: Use SIEM systems to monitor security events and detect suspicious activity.
- Threat intelligence platforms: Leverage threat intelligence to stay ahead of emerging threats and proactively protect against known vulnerabilities.
These advanced tools provide an additional layer of defense, working in conjunction with basic security measures to create a robust and comprehensive security strategy.
Conclusion
The threat to Office365 executive inboxes is real and escalating. The sophistication of attacks, combined with the high value of the data they target, results in significant financial losses for organizations of all sizes. Protecting your Office365 executive inboxes requires a proactive and multi-layered approach. By implementing robust security measures, investing in advanced security solutions, and regularly training your employees, you can significantly reduce your risk and protect your organization from the devastating consequences of a breach. Secure your Office365 accounts, protect your executive inboxes, and strengthen your Office365 security today. Don't wait until it's too late. Learn more about protecting your organization by visiting [link to relevant resource].

Featured Posts
-
 The Risky Business Uncovering The Alterations To Princess Dianas Iconic Met Gala Dress
May 06, 2025
The Risky Business Uncovering The Alterations To Princess Dianas Iconic Met Gala Dress
May 06, 2025 -
 Broadcoms V Mware Deal An Extreme Price Hike Of 1 050 According To At And T
May 06, 2025
Broadcoms V Mware Deal An Extreme Price Hike Of 1 050 According To At And T
May 06, 2025 -
 House Democrats Public Battle The Issue Of Senior Leadership
May 06, 2025
House Democrats Public Battle The Issue Of Senior Leadership
May 06, 2025 -
 Mindy Kaling Stuns Fans With Transformed Figure At Series Premiere
May 06, 2025
Mindy Kaling Stuns Fans With Transformed Figure At Series Premiere
May 06, 2025 -
 O Relacionamento Secreto De Mindy Kaling Detalhes Sobre O Namoro Com Ex Colega De The Office
May 06, 2025
O Relacionamento Secreto De Mindy Kaling Detalhes Sobre O Namoro Com Ex Colega De The Office
May 06, 2025
Latest Posts
-
 Eksport Trotylu Z Polski Analiza Duzego Zamowienia
May 06, 2025
Eksport Trotylu Z Polski Analiza Duzego Zamowienia
May 06, 2025 -
 Trotyl Z Polski Dla Amerykanskiej Armii Nowy Kontrakt
May 06, 2025
Trotyl Z Polski Dla Amerykanskiej Armii Nowy Kontrakt
May 06, 2025 -
 Kontrowersyjne Zamowienie Trotylu Polska Na Celowniku
May 06, 2025
Kontrowersyjne Zamowienie Trotylu Polska Na Celowniku
May 06, 2025 -
 Kontrakty Zbrojeniowe Polska Dostarczy Trotyl Usa
May 06, 2025
Kontrakty Zbrojeniowe Polska Dostarczy Trotyl Usa
May 06, 2025 -
 Wielkie Zamowienie Na Trotyl Z Polski Szczegoly Kontraktu
May 06, 2025
Wielkie Zamowienie Na Trotyl Z Polski Szczegoly Kontraktu
May 06, 2025
