Post-Quantum Cryptography Market To Reach Billions By 2030: Impact Of New Standards And Migration Timelines
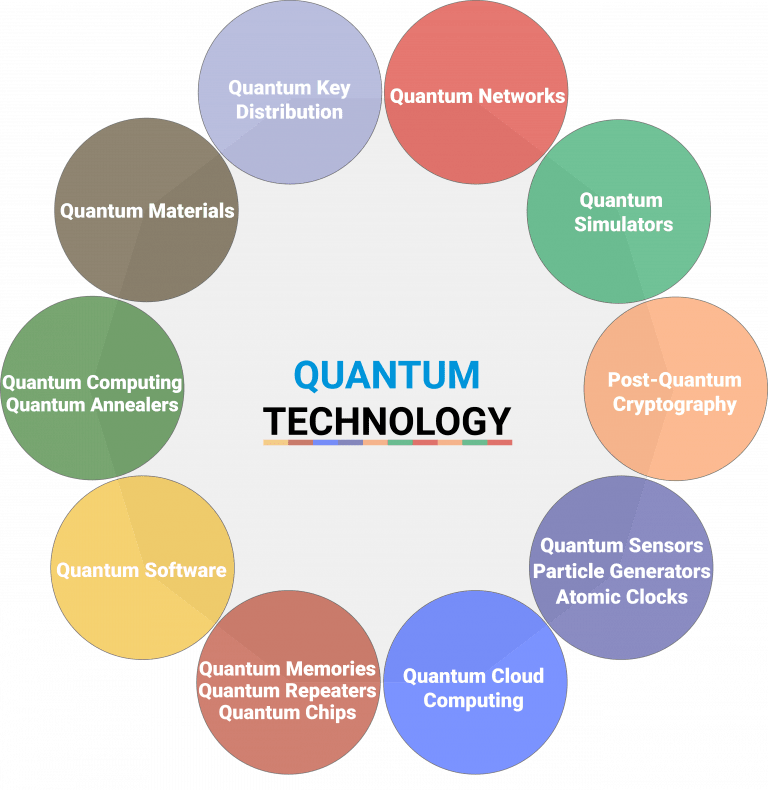
Table of Contents
The Rise of Quantum Computing and the Threat to Current Encryption
Quantum computers, leveraging the principles of quantum mechanics, possess the computational power to crack widely used encryption algorithms far faster than classical computers. RSA, relying on the difficulty of factoring large numbers, and ECC, based on the elliptic curve discrete logarithm problem, are both susceptible. This poses significant security risks across numerous sectors.
- RSA vulnerability timeline: While the exact timeline is uncertain, experts predict that sufficiently powerful quantum computers could break commonly used RSA keys within the next decade or two.
- ECC vulnerability timeline: Similar vulnerabilities exist for ECC, with the potential for decryption becoming a reality as quantum computing advances.
- Impact on data security and privacy: The successful breach of encryption could lead to widespread data theft, identity theft, financial losses, and erosion of public trust.
- Examples of industries most at risk: Finance (banking, payments), healthcare (patient records), government (national security), and critical infrastructure are particularly vulnerable.
Emerging Post-Quantum Cryptography Standards and Algorithms
The National Institute of Standards and Technology (NIST) has been spearheading the effort to standardize post-quantum cryptographic algorithms, leading to a crucial step in securing our digital future. After a rigorous selection process, several algorithms have emerged as finalists, offering varying strengths and weaknesses:
- CRYSTALS-Kyber: A key-establishment algorithm known for its relatively fast performance and strong security.
- FALCON: A digital signature algorithm offering a good balance between security and efficiency.
- SPHINCS+: A digital signature algorithm offering the highest level of security but with a larger signature size and slower performance.
Key features of each selected algorithm: Each algorithm offers unique characteristics regarding key size, signature size, speed of encryption and decryption, and security level against known quantum attacks.
Comparison table of different algorithms (security level, performance): NIST provides detailed comparative analysis of the selected algorithms to help organizations choose the best fit for their specific needs. Consider factors like performance overhead, key sizes, and the type of cryptographic operations required.
Expected adoption rate of different algorithms: The adoption rate will likely vary depending on factors such as industry requirements, ease of integration, and perceived security benefits. CRYSTALS-Kyber, due to its efficiency, might see wider adoption early on.
Key Players in the Post-Quantum Cryptography Market
The development and implementation of post-quantum cryptography solutions involve a diverse range of players:
- Prominent companies: Major technology companies like Google, Microsoft, and IBM, are actively involved in research and development, driving advancements in post-quantum cryptography.
- Their contributions to the post-quantum cryptography ecosystem: These companies contribute through research, developing software libraries, and integrating post-quantum algorithms into their products.
- Examples of their post-quantum solutions: Many companies are offering software development kits (SDKs) and libraries to ease the transition for developers.
Migration Timelines and Challenges in Implementing Post-Quantum Cryptography
Migrating to post-quantum cryptography is a complex undertaking, presenting significant challenges:
- Technical challenges of implementation: Updating existing systems requires substantial technical expertise and careful planning. Compatibility with legacy systems needs careful consideration.
- Cost implications of migration: The cost of upgrading software and hardware, conducting security audits, and retraining staff can be substantial.
- Interoperability issues: Ensuring seamless communication between systems using different post-quantum algorithms is crucial.
- Importance of security audits and risk assessments: Thorough risk assessments are necessary to identify vulnerabilities and prioritize migration efforts.
A phased approach, starting with the most critical systems, is recommended.
Market Projections and Growth Opportunities in Post-Quantum Cryptography
The post-quantum cryptography market is expected to experience significant growth, driven by several factors:
- Market segmentation by industry: The market is segmented across various sectors, including finance, healthcare, government, and technology.
- Regional market analysis: Growth will vary across different regions, depending on technological advancement, regulatory frameworks, and levels of cybersecurity awareness.
- Forecast for different post-quantum cryptography solutions: Different algorithms and solutions will have varied market shares, depending on performance and ease of implementation.
- Investment opportunities in the sector: Significant investment opportunities exist for companies developing, implementing, and supporting post-quantum cryptography solutions.
Conclusion: Securing the Future with Post-Quantum Cryptography
The post-quantum cryptography market is experiencing rapid expansion, driven by the looming threat of quantum computing and the emergence of new standards. Timely migration to post-quantum cryptography solutions is no longer a future consideration; it's a present necessity. Don't wait; start your post-quantum cryptography migration now! Invest in post-quantum cryptography solutions today to secure your future and safeguard your valuable data from the impending quantum threat. Learn more about post-quantum cryptography and develop a robust migration strategy to protect your organization from the vulnerabilities of current encryption methods.

Featured Posts
-
 Xrs Next Frontier How Ai First Devices Will Reshape The Competitive Landscape
May 13, 2025
Xrs Next Frontier How Ai First Devices Will Reshape The Competitive Landscape
May 13, 2025 -
 Best Senior Trips Activities And Events Calendar
May 13, 2025
Best Senior Trips Activities And Events Calendar
May 13, 2025 -
 Southern California Mini Heat Wave What To Expect This Weekend
May 13, 2025
Southern California Mini Heat Wave What To Expect This Weekend
May 13, 2025 -
 No New Elsbeth On March 20th When To Expect Season 2 Episode 16
May 13, 2025
No New Elsbeth On March 20th When To Expect Season 2 Episode 16
May 13, 2025 -
 I See Murder An Elsbeth Season 2 Preview
May 13, 2025
I See Murder An Elsbeth Season 2 Preview
May 13, 2025
Latest Posts
-
 Byd Challenges Fords Legacy Expanding Ev Dominance In Brazil
May 13, 2025
Byd Challenges Fords Legacy Expanding Ev Dominance In Brazil
May 13, 2025 -
 Byds Rise Fords Decline Opens Door For Chinese Ev Giant In Brazil
May 13, 2025
Byds Rise Fords Decline Opens Door For Chinese Ev Giant In Brazil
May 13, 2025 -
 Promosi Terhad Tempah Byd Ev Di Mas 2025 And Terima Rm 800 Kredit Cas 9 15 Mei Konsert Menarik Menanti
May 13, 2025
Promosi Terhad Tempah Byd Ev Di Mas 2025 And Terima Rm 800 Kredit Cas 9 15 Mei Konsert Menarik Menanti
May 13, 2025 -
 Dapatkan Rm 800 Kredit Cas Sempena Tempahan Byd Ev Di Mas 2025 9 15 Mei Konsert Rentak Elektrik
May 13, 2025
Dapatkan Rm 800 Kredit Cas Sempena Tempahan Byd Ev Di Mas 2025 9 15 Mei Konsert Rentak Elektrik
May 13, 2025 -
 Jom Tempah Byd Ev Di Pameran Automotif Mas 2025 Rm 800 Kredit Cas Menanti 9 15 Mei
May 13, 2025
Jom Tempah Byd Ev Di Pameran Automotif Mas 2025 Rm 800 Kredit Cas Menanti 9 15 Mei
May 13, 2025
