Millions Made From Office365 Breaches: Insider Threat Exposed
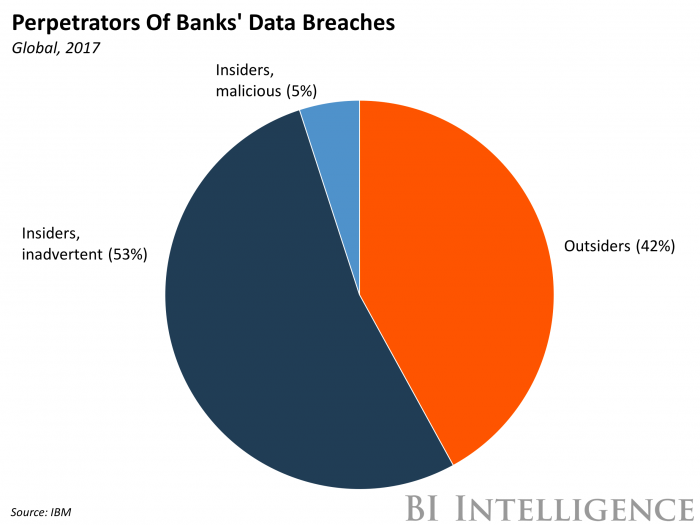
Table of Contents
The Growing Threat of Insider Attacks on Office365
The rise of cloud computing and the increasing reliance on platforms like Office365 have unfortunately broadened the attack surface for malicious actors. While external threats remain a concern, the threat of insider attacks on Office365 is escalating rapidly. This is because insiders, by definition, already possess legitimate access to sensitive data and systems.
Types of Insider Threats:
-
Malicious Insiders (Intentional Data Breaches): These individuals actively seek to steal data for personal gain, such as selling confidential information or intellectual property to competitors. Their motivations are often financial, driven by greed or blackmail.
-
Negligent Insiders (Accidental Data Leaks): These individuals unintentionally compromise security through careless actions. This might involve clicking on a phishing link, leaving their laptop unattended, or failing to follow security protocols. Their actions, while not malicious, can have devastating consequences.
-
Compromised Insiders (Phishing and Malware): Insiders can become unwitting accomplices when their accounts are compromised through phishing attacks or malware infections. This allows attackers to leverage their existing access to infiltrate the system and exfiltrate data.
Motivations behind Insider Threats: Beyond financial gain, insider threats are also motivated by revenge, disgruntled employees seeking to damage their former employer, or even ideological reasons.
Statistics: While precise figures vary, studies suggest that a significant percentage (estimates range from 30% to 60%) of data breaches involve insider threats. The cost of these breaches is substantial, leading to financial losses, legal fees, reputational damage, and loss of customer trust. One notable example is the case of [insert real-world example of an Office365 insider threat breach and its consequences here].
Common Tactics Used in Office365 Insider Breaches
Understanding the methods employed by attackers is crucial for effective defense. Several common tactics target vulnerabilities in Office365 security.
Exploiting Weak Passwords and Multi-Factor Authentication (MFA) Bypass:
- Password Spraying and Brute-Force Attacks: Attackers attempt to guess passwords using common combinations or automated tools. Weak passwords, especially those reused across multiple platforms, make this tactic highly effective.
- Importance of Strong Passwords and MFA: Implementing strong, unique passwords and mandating multi-factor authentication (MFA) significantly reduces the risk of unauthorized access.
- MFA Bypass Techniques: While MFA adds a significant layer of security, attackers continually seek ways to bypass it, such as using phishing techniques to obtain MFA codes or exploiting vulnerabilities in MFA implementation.
Phishing and Social Engineering:
- Targeting Employees: Phishing emails often impersonate legitimate sources, such as IT support or company executives, aiming to trick employees into revealing their Office365 credentials.
- Convincing Phishing Emails: These emails are increasingly sophisticated, using personalized details and urgent requests to increase their effectiveness.
- Detection and Avoidance: Regular security awareness training is crucial to teach employees how to identify and report suspicious emails and links.
Malware and Ransomware Attacks:
- Gaining Access: Malware can be used to steal credentials, install keyloggers, or grant remote access to an attacker. This malware can be delivered through phishing emails or malicious attachments.
- Impact of Ransomware: Ransomware can encrypt sensitive data stored in Office365, disrupting operations and demanding a ransom for its release.
- Prevention and Response: Regular software updates, robust antivirus solutions, and incident response plans are essential to mitigate the impact of malware and ransomware.
Protecting Your Organization from Office365 Insider Threats
A multi-layered approach combining technical controls and employee awareness is vital for effective protection.
Implementing Robust Security Measures:
- Strong Password Policies and MFA: Enforce strong password policies and mandate MFA for all users.
- Security Awareness Training: Regular training programs educate employees about phishing scams, malware, and safe online practices.
- Advanced Threat Protection Tools: Invest in advanced threat protection tools that monitor user activity, detect anomalies, and block malicious attacks.
- Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses.
Access Control and Data Loss Prevention (DLP):
- Least Privilege Access: Implement the principle of least privilege, granting users only the necessary access rights to perform their jobs.
- DLP Tools: Utilize DLP tools to monitor and prevent sensitive data from leaving the organization's control.
- Regular Permission Reviews: Regularly review and update user permissions and access rights.
Incident Response Planning:
- Comprehensive Plan: Develop a comprehensive incident response plan outlining steps to take in case of a security breach.
- Clear Communication: Establish clear communication protocols for notifying relevant stakeholders during a security incident.
- Regular Testing: Regularly test and update the incident response plan to ensure its effectiveness.
Millions Made from Office365 Breaches: Protecting Your Business
The financial risks associated with Office365 breaches caused by insider threats are substantial. Weak passwords, phishing attacks, and malware are common entry points for attackers. A multi-layered security approach, combining strong technical controls with comprehensive employee training, is crucial for mitigating these risks. Don't become another statistic in the millions lost annually to Office365 insider threats. Implement the security measures outlined in this article and protect your organization. For further assistance in securing your Office365 environment, [link to relevant resources, e.g., security assessments, training materials].

Featured Posts
-
 Analysis The Likelihood Of A Fifth Champions League Place For The Premier League
Apr 29, 2025
Analysis The Likelihood Of A Fifth Champions League Place For The Premier League
Apr 29, 2025 -
 Jan 6 Witness Cassidy Hutchinson Announces Fall Memoir Release
Apr 29, 2025
Jan 6 Witness Cassidy Hutchinson Announces Fall Memoir Release
Apr 29, 2025 -
 January 6th And The Epps Fox News Defamation Case A Deep Dive Into The Allegations
Apr 29, 2025
January 6th And The Epps Fox News Defamation Case A Deep Dive Into The Allegations
Apr 29, 2025 -
 Nyt Strands Hints And Answers Monday March 31 Game 393
Apr 29, 2025
Nyt Strands Hints And Answers Monday March 31 Game 393
Apr 29, 2025 -
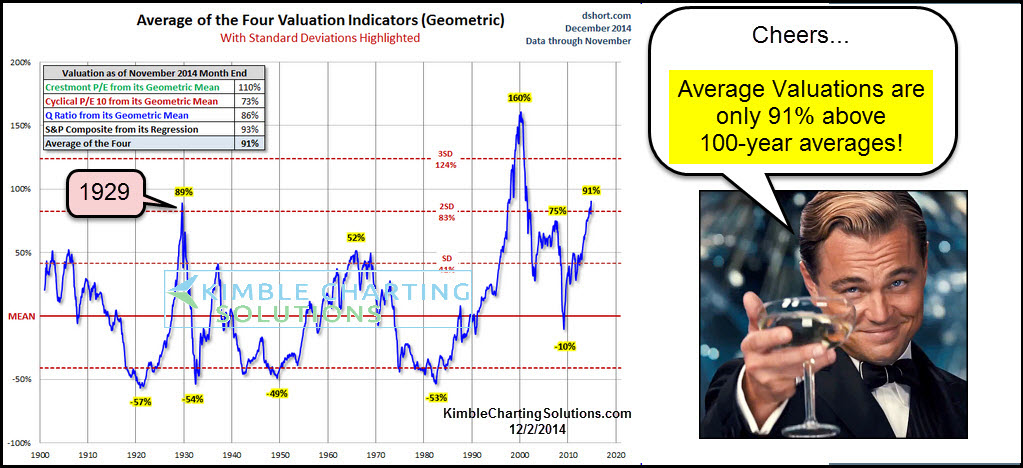 High Stock Market Valuations Why Bof A Believes Investors Shouldnt Worry
Apr 29, 2025
High Stock Market Valuations Why Bof A Believes Investors Shouldnt Worry
Apr 29, 2025
Latest Posts
-
 Baseball Legend Johnny Damon Trump Is Right Pete Rose Belongs In The Hall Of Fame
Apr 29, 2025
Baseball Legend Johnny Damon Trump Is Right Pete Rose Belongs In The Hall Of Fame
Apr 29, 2025 -
 Johnny Damon Pete Rose In Baseball Hall Of Fame Agrees With Trump
Apr 29, 2025
Johnny Damon Pete Rose In Baseball Hall Of Fame Agrees With Trump
Apr 29, 2025 -
 Trump To Pardon Pete Rose After His Death Analyzing The Announcement
Apr 29, 2025
Trump To Pardon Pete Rose After His Death Analyzing The Announcement
Apr 29, 2025 -
 Will Pete Rose Receive A Posthumous Pardon From Trump
Apr 29, 2025
Will Pete Rose Receive A Posthumous Pardon From Trump
Apr 29, 2025 -
 Pete Rose Pardon Trumps Statement And Its Implications
Apr 29, 2025
Pete Rose Pardon Trumps Statement And Its Implications
Apr 29, 2025
