Millions Stolen Through Office365: How A Hacker Targeted Executives
Table of Contents
The Hacker's Methodology: Exploiting Weak Links in Office365 Security
This sophisticated attack leveraged multiple techniques to gain access to sensitive information and ultimately, millions of dollars. The hackers exploited vulnerabilities in the organization's Office365 security protocols, demonstrating the importance of layered security.
Phishing and Spear Phishing Attacks
The initial breach involved a series of highly targeted phishing and spear phishing attacks. These emails were meticulously crafted to bypass traditional email security filters and appear legitimate to unsuspecting executives.
- Sophisticated Emails: Emails mimicked communications from known business partners, containing seemingly innocuous attachments or links.
- Bypassing Security: The hackers employed techniques like using reputable domains and embedding malicious code in seemingly harmless files.
- Successful Subject Lines & Content: Examples included urgent requests for financial information, fake invoices, and requests to approve urgent payments.
- Common Tactics:
- Creating a sense of urgency.
- Impersonating trusted individuals or organizations.
- Using convincing email addresses and logos.
- Including seemingly legitimate attachments containing malware.
Exploiting Credential Stuffing and Brute-Force Attacks
In addition to phishing, the hackers employed credential stuffing and brute-force attacks. This involved attempting to guess or crack passwords using publicly available information or automated tools.
- Weak Passwords: The reuse of passwords across multiple platforms significantly increased vulnerability.
- Password Reuse: Many executives reused personal passwords for their work accounts.
- MFA's Importance: Multi-factor authentication (MFA) would have significantly mitigated the success of these attacks.
- Effectiveness of Security Measures:
- Multi-factor authentication (MFA) adds an extra layer of security, requiring multiple forms of verification.
- Password managers generate strong, unique passwords for each account, reducing the risk of credential stuffing.
Leveraging Social Engineering Techniques
The hackers didn't rely solely on technical exploits; they also employed sophisticated social engineering techniques. This involved manipulating human psychology to gain access to sensitive information.
- Pretexting and Manipulation: Hackers pretended to be legitimate employees or IT support staff to gain trust and access.
- Information Gathering: They used publicly available information on social media and company websites to craft convincing scenarios.
- Security Awareness Training: Lack of comprehensive security awareness training left executives vulnerable to these manipulations.
- Best Practices to Avoid Social Engineering:
- Verify the identity of anyone requesting sensitive information.
- Never click on suspicious links or open attachments from unknown senders.
- Report suspicious emails or phone calls immediately.
The Impact of the Office365 Breach: Financial and Reputational Damage
The consequences of the Office365 security breach were far-reaching, impacting the company's finances, reputation, and legal standing.
Financial Losses
The attack resulted in the theft of millions of dollars, causing significant financial damage.
- Direct Financial Losses: Millions were directly stolen through fraudulent transactions.
- Remediation Costs: The cost of investigating the breach, restoring systems, and implementing new security measures was substantial.
- Legal Fees: The organization incurred significant legal fees associated with investigations and potential lawsuits.
- Financial Repercussions:
- Loss of revenue due to business disruption.
- Increased insurance premiums.
- Damage to investor confidence.
Reputational Damage
The breach severely damaged the company's reputation and eroded customer trust.
- Negative Publicity: The breach generated negative media coverage, damaging the company's public image.
- Loss of Customer Trust: Customers lost faith in the company's ability to protect their data.
- Business Disruptions: The breach led to business disruptions and lost opportunities.
- Reputational Damage:
- Decreased customer loyalty.
- Difficulty attracting new clients.
- Negative impact on employee morale.
Legal and Regulatory Consequences
The company faced significant legal and regulatory consequences.
- Legal Liabilities: The company faced potential lawsuits from affected parties.
- Regulatory Fines: The breach potentially violated data protection regulations (GDPR, CCPA), leading to substantial fines.
- Incident Response Planning: The lack of a robust incident response plan exacerbated the damage.
- Legal and Regulatory Considerations:
- Compliance with data breach notification laws.
- Potential civil and criminal penalties.
- Reputational risks associated with non-compliance.
Strengthening Office365 Security: Preventative Measures and Best Practices
Preventing future Office365 security breaches requires a multi-layered approach.
Implementing Multi-Factor Authentication (MFA)
MFA is critical in enhancing Office365 security.
- Enhanced Security: MFA adds a significant layer of protection against unauthorized access.
- Various MFA Methods: Options include one-time codes, biometric authentication, and security keys.
- Implementation Steps: Enable MFA for all user accounts, especially executives.
- MFA Best Practices:
- Use a variety of MFA methods.
- Educate users on the importance of MFA.
- Regularly review and update MFA settings.
Regular Security Awareness Training
Investing in regular security awareness training is crucial.
- Cybersecurity Threats: Train employees to recognize phishing attempts and social engineering techniques.
- Phishing Awareness: Conduct regular phishing simulations to test employee awareness.
- Effective Training Programs: Use interactive modules, real-world examples, and regular refresher courses.
- Security Awareness Training Strategies:
- Tailor training to different roles and responsibilities.
- Use a variety of training methods.
- Regularly assess employee knowledge and understanding.
Advanced Threat Protection (ATP)
ATP plays a significant role in proactive threat detection and prevention.
- Advanced Threats: ATP helps detect and block advanced threats that bypass traditional security measures.
- Office365 Benefits: ATP enhances Office365 security by analyzing emails, files, and links for malicious content.
- ATP Configuration: Configure ATP to meet the specific needs of the organization.
- Key Features and Benefits of ATP:
- Anti-phishing protection.
- Malware detection and prevention.
- Real-time threat analysis.
Conclusion
This case study demonstrates the devastating consequences of an Office365 security breach, highlighting the critical need for proactive security measures. The hackers’ sophisticated use of phishing, credential stuffing, and social engineering techniques resulted in millions of dollars in losses and irreparable reputational damage. To avoid becoming the next victim, organizations must implement robust security practices. This includes mandatory multi-factor authentication, comprehensive security awareness training for all employees, and the deployment of advanced threat protection for Office365. Don't become the next victim of an Office365 security breach. Take action today to strengthen your defenses and protect your valuable data. Implement robust security measures, including multi-factor authentication, comprehensive security awareness training, and advanced threat protection for Office365.

Featured Posts
-
 Chinas Nuclear Power Push 10 Reactor Approvals Signal Major Growth
Apr 29, 2025
Chinas Nuclear Power Push 10 Reactor Approvals Signal Major Growth
Apr 29, 2025 -
 Black Hawk Pilots Fatal Decision Ignoring Co Pilot Before Collision
Apr 29, 2025
Black Hawk Pilots Fatal Decision Ignoring Co Pilot Before Collision
Apr 29, 2025 -
 Data Breach Exposes Millions In Losses From Compromised Office365 Accounts
Apr 29, 2025
Data Breach Exposes Millions In Losses From Compromised Office365 Accounts
Apr 29, 2025 -
 Solve The Nyt Spelling Bee April 27 2025 Clues And Strategies
Apr 29, 2025
Solve The Nyt Spelling Bee April 27 2025 Clues And Strategies
Apr 29, 2025 -
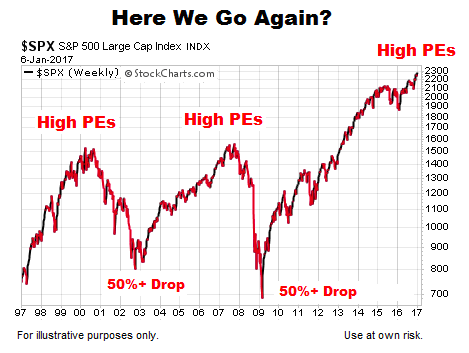 Understanding Elevated Stock Market Valuations A Bof A Analysis
Apr 29, 2025
Understanding Elevated Stock Market Valuations A Bof A Analysis
Apr 29, 2025
Latest Posts
-
 Pete Rose And The Presidential Pardon Sports Betting And The Law
Apr 29, 2025
Pete Rose And The Presidential Pardon Sports Betting And The Law
Apr 29, 2025 -
 The Pete Rose Pardon Trumps Decision And The Future Of Mlb
Apr 29, 2025
The Pete Rose Pardon Trumps Decision And The Future Of Mlb
Apr 29, 2025 -
 Mlbs Pete Rose Ban Trumps Criticism And Promise Of A Posthumous Pardon
Apr 29, 2025
Mlbs Pete Rose Ban Trumps Criticism And Promise Of A Posthumous Pardon
Apr 29, 2025 -
 Will Trump Pardon Pete Rose Examining The Implications Of A Baseball Betting Ban
Apr 29, 2025
Will Trump Pardon Pete Rose Examining The Implications Of A Baseball Betting Ban
Apr 29, 2025 -
 Mlb Considers Petition To Reinstate Pete Rose Report
Apr 29, 2025
Mlb Considers Petition To Reinstate Pete Rose Report
Apr 29, 2025
